
Big data, cloud computing, network virtualization, machine learning, telemetry, and so on; all large fields with immense potential, and boasting wide application in the world of IoT. But all this technical jargon, emanating from different industries, can risk overcomplicating our comprehension of the IoT. To understand the IoT’s key enablers, it’s first essential to break it down into its basic components.
IoT Assets
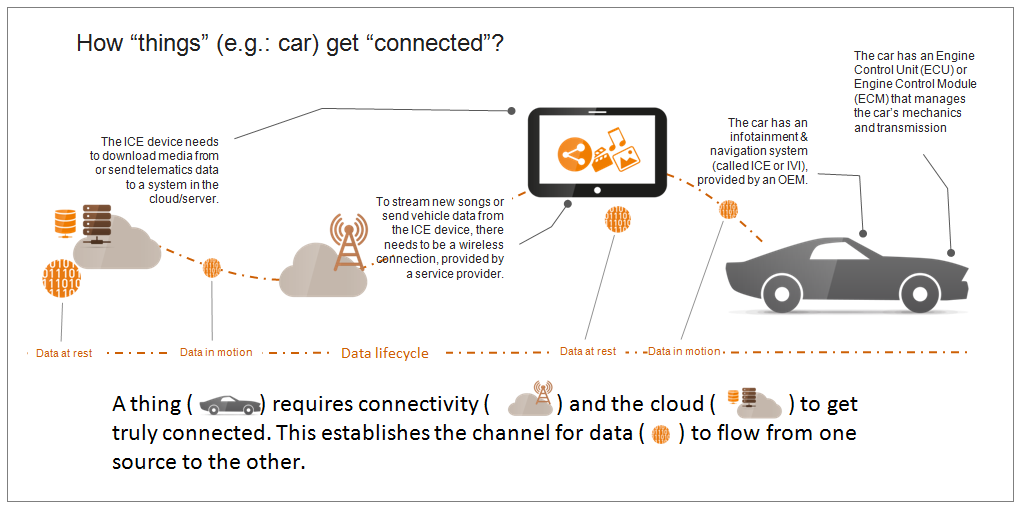
There are three key parts to building a connected application: the device (also known as an endpoint), the connectivity (network infrastructure), and the cloud. The endpoints come in various shapes and sizes, ranging from connected vehicles to smartwatches. Regardless, the true potential of a connected ecosystem can only be achieved if multiple endpoints are working in tandem, or within a cloud infrastructure. To illustrate the point, imagine the data from many different vehicles’ tires sent to a cloud server, where it’s processed by the automaker or tire manufacturer to improve the tire performance, or gain insights which could be used to enhance the future design of the tires. All this information could be exchanged over a cellular network.
If you dissect these three parts, you can imagine each being a constituent of three core components: hardware, software and data. In another example, an endpoint, such as a smartwatch (hardware), would have some apps (software) on it, each producing some amount of data (calories, steps walked, call data, etc.).
Connectivity infrastructure uses routers (hardware) with some embedded operating system and applications (software), and data (routing tables, alerts etc.). The cloud too, is built on hardware (servers), software (operating system, ERP applications etc.) and loads of data. These components have to be understood to appreciate the true nature of the IoT.
Key Enablers of Trust
With so many stakeholders, enabling trust is critical for the ecosystem to thrive. There are three key enablers for building trust in IoT:
Connectivity is an inherent part of the Internet. If an IoT asset needs to be connected to another, reliable connectivity is pivotal. From simple streaming of songs to mission-critical cases like the eCall, connectivity can make or break the behavior of a connected device. The right building blocks will help stakeholders ensure endpoints of different sizes can be reliably connected, while the quality of service (QoS) can be monitored to enable reliable exchange of data between multiple endpoints, or an endpoint and the cloud.
Software and data is becoming increasingly crucial to our everyday lives. The potential of billions of connected endpoints also opens up new opportunities for cyber-criminals. They will try to exploit the vulnerabilities in the different hardware, software and data assets, whether on the devices, in the cloud, or over the network.
The security infrastructure in IoT requires a special focus on managing the lifecycle of security components. Numerous IoT devices or endpoints like vehicles, watches, healthcare devices etc. could either be on the move or be deployed in such remote areas that they cannot be easily serviced.
Whether it’s about managing endpoint identities, encryption keys, embedded software, or data, a reliable and scalable security framework is pivotal to ensuring every stakeholder’s software, hardware and data assets are secured.
Otherwise, there will be inevitable breaches, resulting in a trust deficit. To learn more about IoT security, download our ebook, or visit our dedicated webpage.
Mostly overlooked because of the hype, an agile monetization framework is crucial for the IoT to thrive. The global nature of IoT is such that the assets used to set up a connected infrastructure could come from many different parts of the world. The endpoint could be manufactured in Taiwan, its embedded software developed in Bangalore, the cloud infrastructure in Silicon Valley, and the service itself might eventually run in Germany.
How does each contributor ensure that its intellectual property (the IoT asset) is monetized? Where the product (an endpoint) is now being sold as-a-service, how do these individual contributors enable their own monetization as a service strategy?
Consider a Satellite Navigation device running in Germany. The SatNav company may sell its device on a pay-per-month model. But how do all those stakeholders in Taiwan, Bangalore or Silicon Valley implement their own flexible monetization models? In order for the ecosystem to thrive, each stakeholder needs to trust that it can see return on its investment – and this can only be implemented with a proper licensing and entitlement capability that helps protect individual contributions.
Download our latest infographic on our “Connect, Secure, Monetize” approach, and learn some more interesting IoT-related facts. To learn more, write to us on iot.query@gemalto.com, or speak to your local Gemalto representative.


