Drones have been developing with a tremendous pace, having mainly commercial applications in video & photography, agriculture, energy, construction and public safety and rescue. In a recent blog, we looked into the buzz around the drone ecosystem and the security issues that need to be put high on the agenda. We found that the most common drone security issues include collision risks, drone hacking and privacy concerns.
In this post, we are going to look at how we can enable trust in the commercial drone sector by arguing that securing the flow of data within the ecosystem will underpin its success. Key stakeholders in this ecosystem comprise of drone manufacturers and operators who need to protect their assets and services, while public authorities need to ensure citizen safety and law enforcement. We have found there are seven key factors to ensure trust at every stage at the drone ecosystem.
Let’s look into them in more detail.
-
Secure pilot and drone registration
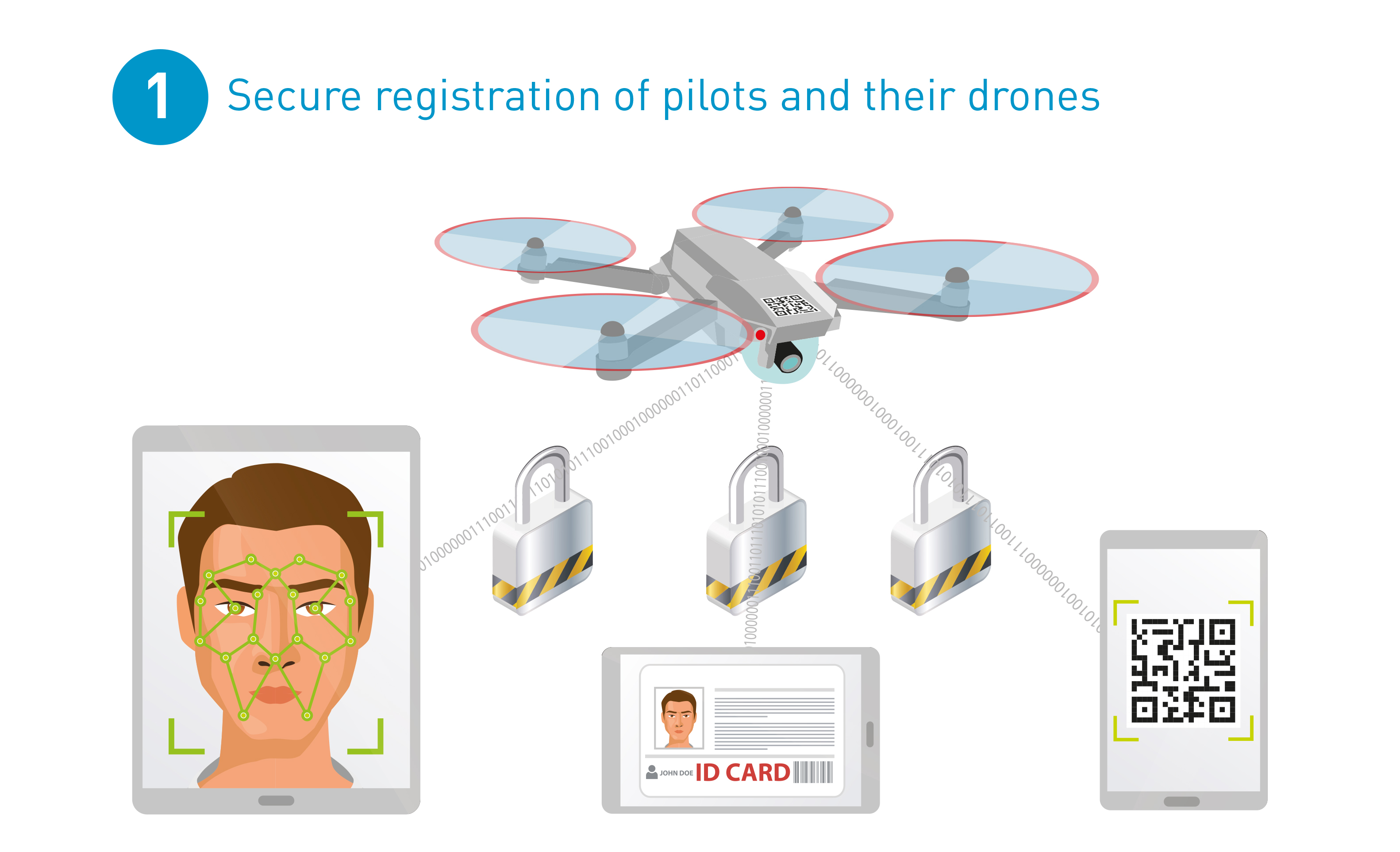
Registering pilots and drones with public authority servers needs to be secure and reliable. Each drone must also be linked to its pilot, in the same way as a car’s license plate links it to a driver. In the case of drones, this is also done for liability purposes. For example, if the drone goes off track, the authorities can contact the pilot immediately.
This can be achieved by using strong pilot ID verification and drone registration, so that pilots and their drone can register remotely and securely.
-
Protection of sensitive data on the drone
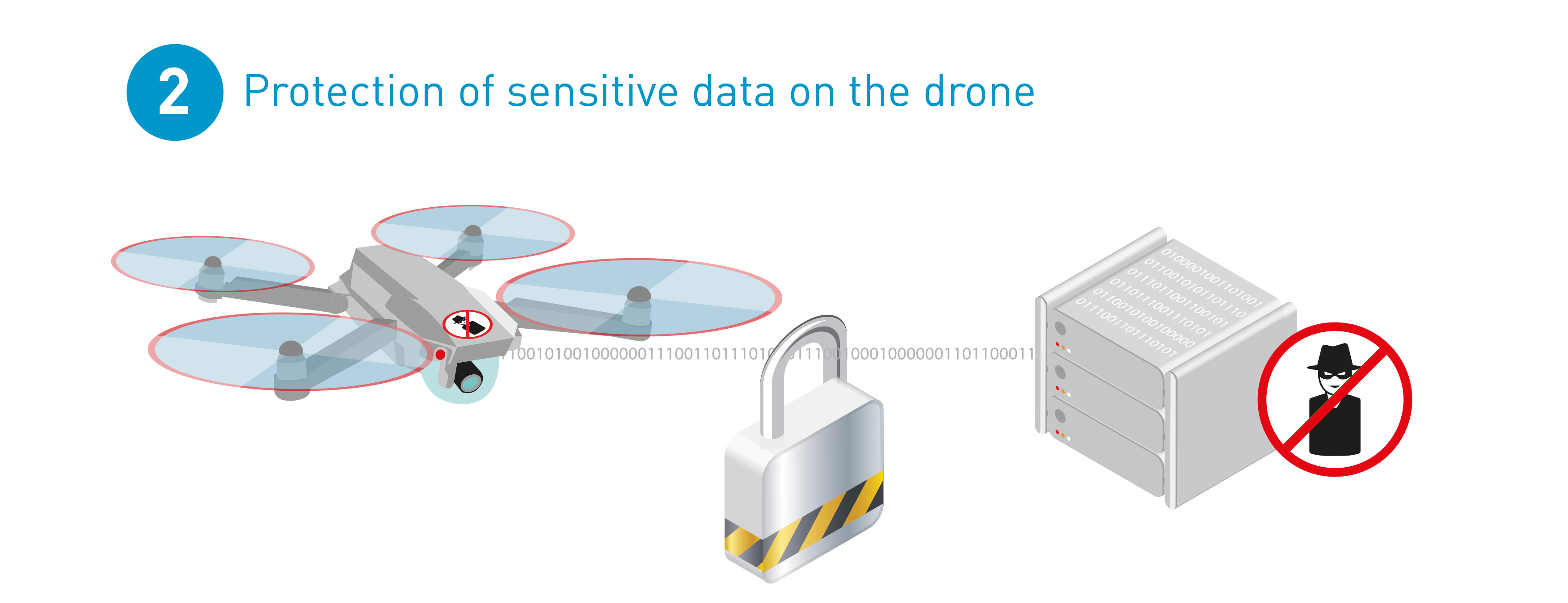
Each commercial drone comes with built-in firmware, which stores sensitive data on the drone, so they can be flown. It includes built-in security features such as forbidden areas, maximum altitudes, and range from take-off, which must be protected from modification. An effective way to protect the integrity of this data would be to store it in hardware tamper proof devices such as secure elements.
-
Seamless and secure connectivity

For easy global deployment, drone manufacturers need their drones to connect seamlessly and securely to networks in all countries. In this regard, capitalizing on GSM networks is particularly adaptable for commercial drones, due to their proven field, secure infrastructure and coverage.
Other benefits of GSM networks include:
- The low latency of last generation of networks, which is crucial for command data to pilot drones or to track them in real-time
- High speed internet, particularly adapted for video streaming for instance
5G networks will further improve those benefits, compared to today’s LTE technology enabling more speed, agility and efficiency.
-
Reliable drone tracking
![]()
Public authorities need to be able to reliably identify drones in real-time, anywhere. To do so, they would need to be able to trust real time tracking data that hasn’t been modified, as being genuine.
Drone tracking data comprises of drone unique identifiers and dynamic data such as location and time stamp. But how to protect this highly-sensitive data? This could be achieved through secure-element-based security and cryptography, which ensure the integrity and proof of origin of the tracking data.
-
Protection of flight control commands
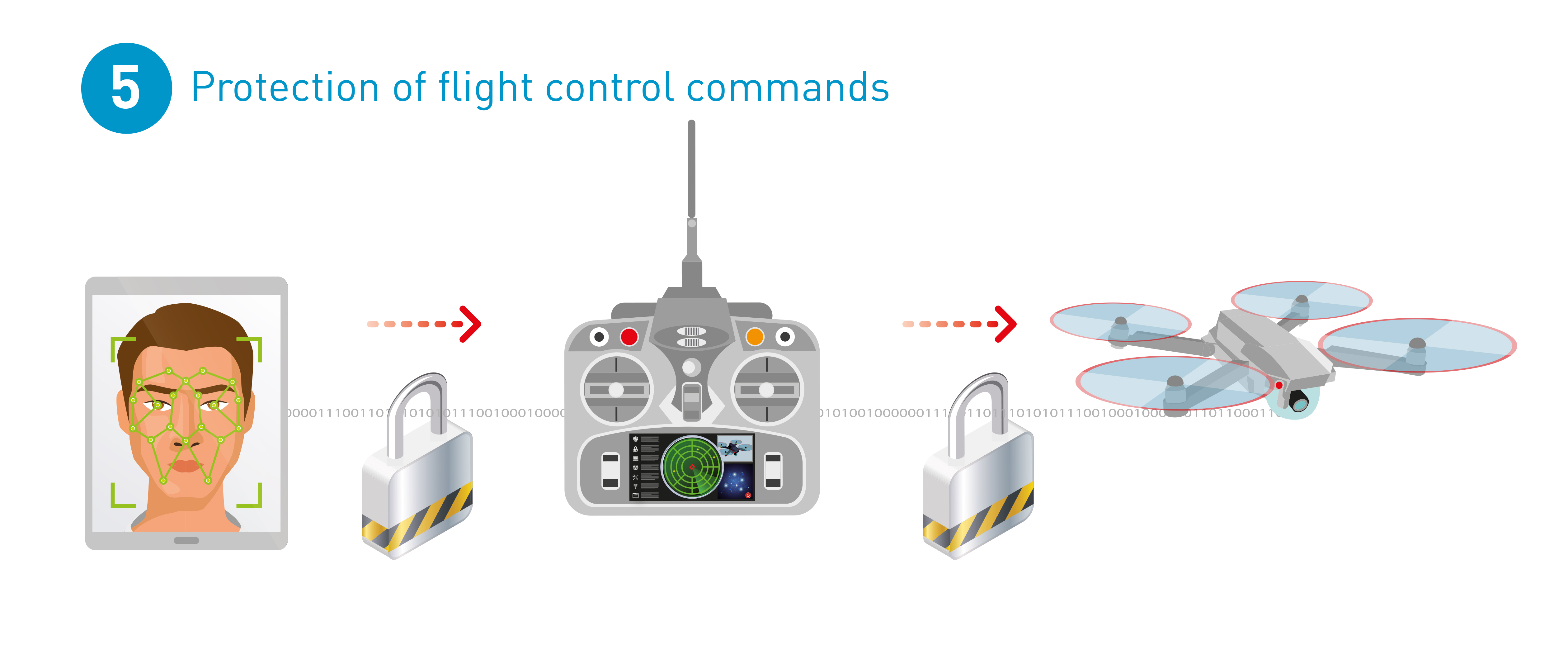
Drones must be controlled by authorized platforms and operated by authorized pilots on the ground, and therefore must be protected against hacking. User-authentication solutions allow for authorized pilots to access the remote-control applications used to control the drones from ground stations or mobile devices.
The protection of flight control command can be achieved by cryptography: securing existing communication channels between the ground stations and the drone by command encryption that is decrypted in real-time by the machine itself. Commands that are not part of the encryption protocol cannot be executed.
6. Confidentiality of data exchange between drones and operators
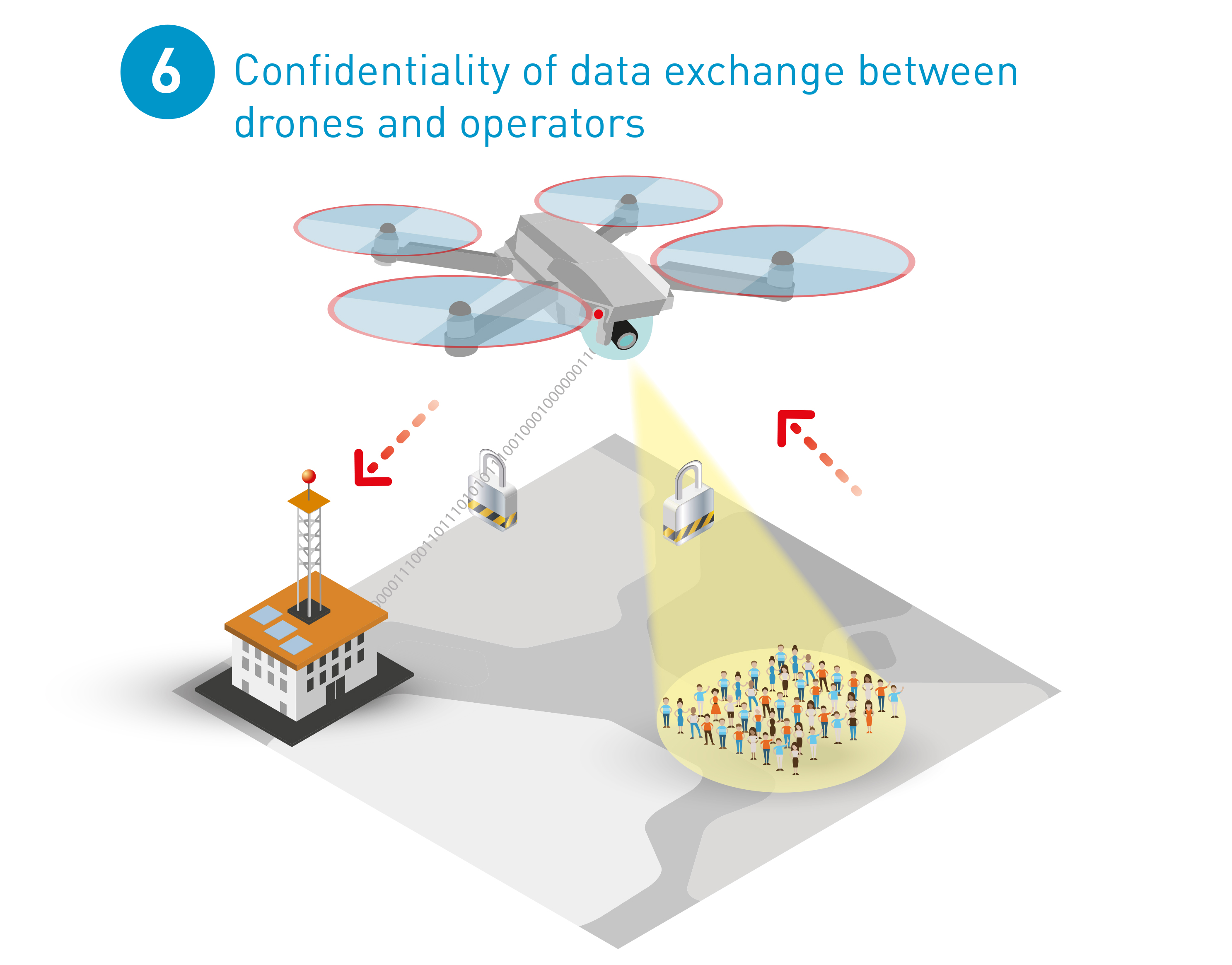
Certain confidential information such as public-safety-related information during rescue operations, must be kept private. The aforementioned encryption technology not only secures the communication channels between the drone and the ground, but also ensures that any exchanged data between the two cannot be accessed by a third party.
-
Flight traceability data
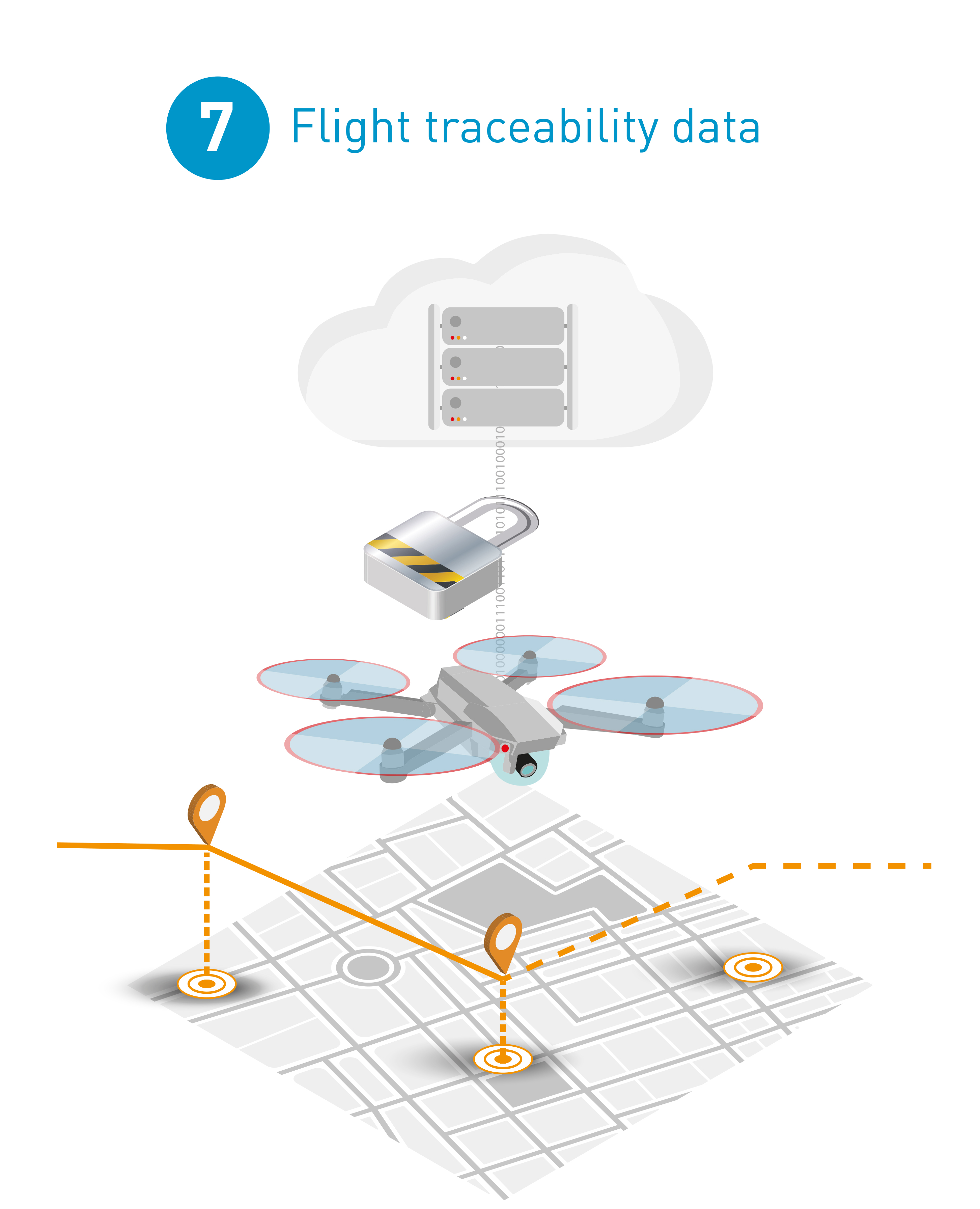
All flight-related data must be securely stored and protected, for investigation or traceability purposes. This can be achieved with the use of secure servers on the cloud.
Discover how our solutions enable trust in the drone ecosystem.
If you have any questions on how to enable trust in the commercial drone ecosystem, do let us know by leaving a comment below or tweeting us @Gemalto.


