With Ericsson predicting that the number of IoT devices connected to cellular networks will reach 3.5 billion by 2023, it is clear that MNOs should be preparing for major new commercial opportunities. Moreover, there can be no doubt that the emergence of the new generation 5G network will be a huge asset in this respect, helping to enable the explosive growth in the number of devices connected both to people and each other. MNOs have a key role to play for the development of IoT devices with cellular connectivity, especially with regards to security.
In this blog, I am joined by my colleague Jean-Francois Gros, Director, Marketing & Strategy at Thales and Chairman of the GSMA IoT SAFE sub group (pictured below), to discuss why eSIM is ideally placed to deliver scalable security for cellular IoT applications.

What are the IoT security challenges that MNOs will need to address?
DB: We are seeing the emergence of ever more security-sensitive services such as telematics for vehicles in the automotive sector, like automatic driving systems, driving assistance systems, GPS navigation, vehicular emergency warning systems, wireless safety communications, and health monitoring in healthcare. Security is a must for these services! According to a Forrester report (Forrester, January 9th 2019), the volume of IoT attacks is rising by well over 200% per annum. At the same time, Irdeto’s 2019 Global Connected Industries survey indicated that 80% of IoT devices used or manufactured by large enterprises have experienced a cyberattack in the past 12 months.
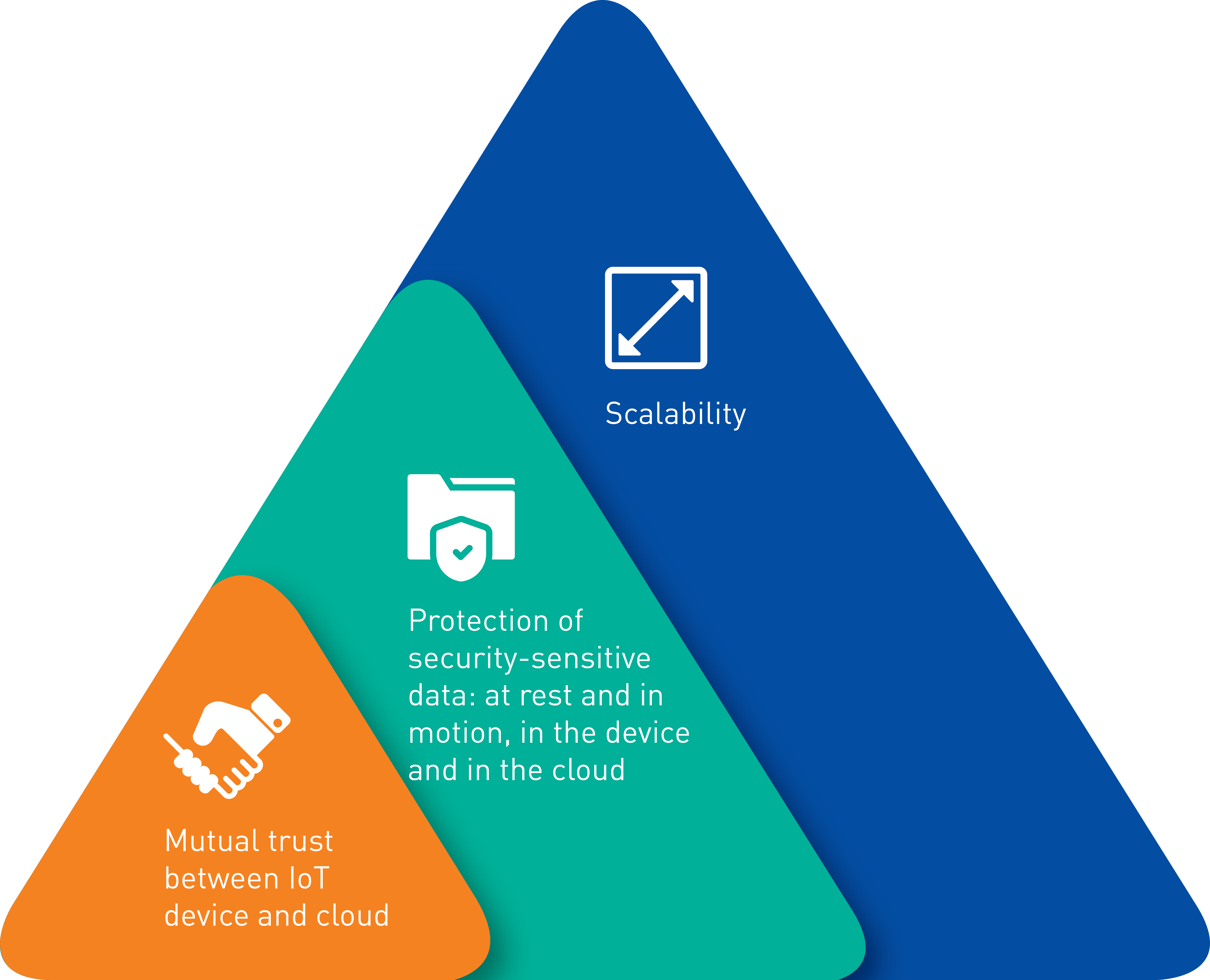
Establishing trust and confidence in the IoT is a top priority for all stakeholders looking to benefit from the new age of connectivity. Essentially, the security framework must fulfil three key requirements. First, mutual authentication between the IoT device and the cloud. Then, integrity and confidentiality of security-sensitive data both at rest and in motion, and last but not least, scalability of security.
JFG: Indeed, the IoT is characterized by fragmentation in terms of the Operating System (OS) deployed. There are a number of open source and proprietary IoT OS already available in the market. Given the variety of applications, hardware and connectivity, encompassed with the IoT, it is likely that the market will continue to sustain multiple OSes for the foreseeable future. In this respect, any IoT security implementation which is dependent on the type of OS would not be able to scale and is therefore not sustainable. This is a key security challenge that MNOs need to address.
Do we need new technologies to address this IoT security fragmentation?
DB: Not quite! In fact, there is an existing technology/framework, which is already proven in the field and is ideally suited for the IoT. This includes secure elements at large and, more specifically, eSIM/SIM in the case of cellular connectivity for the IoT. Indeed, the secure elements can deliver scalable ‘security-by-design’ for the IoT, while eSIM/SIM can deliver scalable IoT security for cellular networks.
JFG: The approach is to leverage on those hardware temper-proof elements, also known as the Root of Trust, to store sensitive data such as keys and security services and to establish a common. Moreover, the secure elements are standard technology and are ideally suited to integrate the new specifications for IoT security from GSMA’s latest specifications: GSMA IoT SAFE (IoT on-SIM Applet For Secure End-2-End Communication). These specifications provide an interoperable and scalable security framework for the IoT. We are the first to implement the GSMA standard specifications for the IoT. This is an unprecedented advance in terms of scalable IoT security for all security-sensitive use cases.
How does IoT SAFE work?
JFG: The IoT device embeds a SIM/eSIM with the Thales IoT SAFE applet (application). As soon as the IoT device is switched on, it is automatically and securely provisioned with its IoT applications (the secure provisioning is performed by the IoT SAFE Security server). From this point, all exchanges between the IoT device are secure and trusted. The server can trust the IoT device and vice-versa and all the exchanges made are secure. All this occurs in a matter of seconds. This means that devices already in the field can be activated with any service provider. This is a great opportunity for Mobile Network Operators who want to offer secure IoT services to leverage on their experience of managing billions of secure elements already in the field through OTA (Over the Air) platforms.
DB: All players in the IoT ecosystem can benefit from this. In particular, device makers can offer devices with embedded scalable security, regardless of the OS and chip fragmentation, and service providers can develop secure services in an interoperable framework. There’s no need for the latter to implement custom security that is dependent on the OS and the chip.
Need more information? Do not hesitate to contact us by tweeting us @Gemalto.



