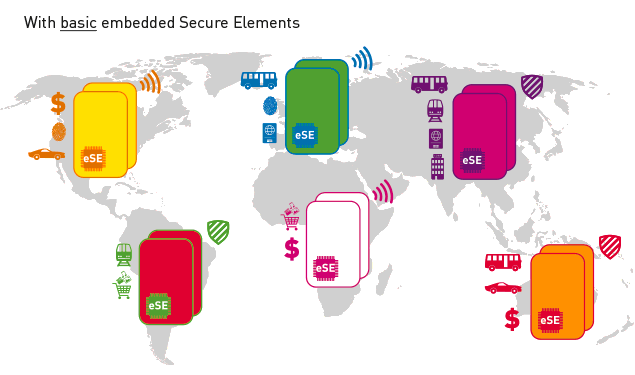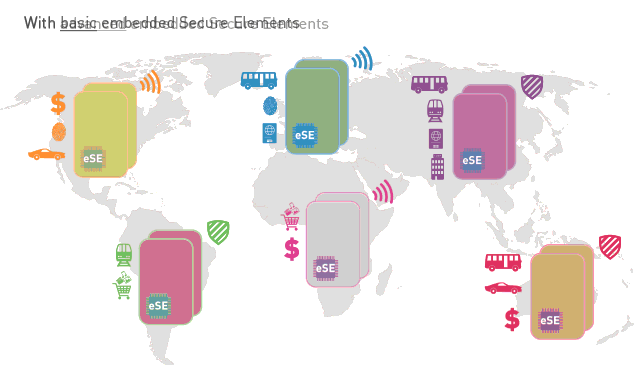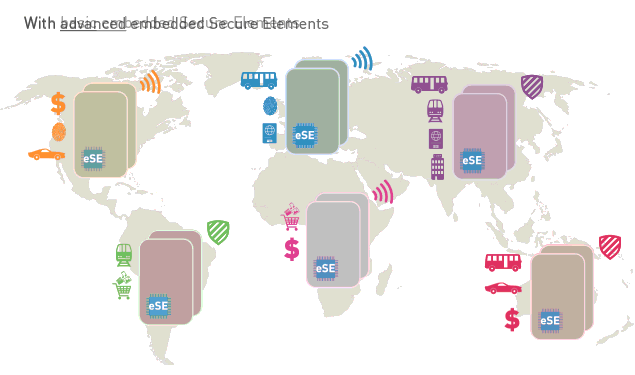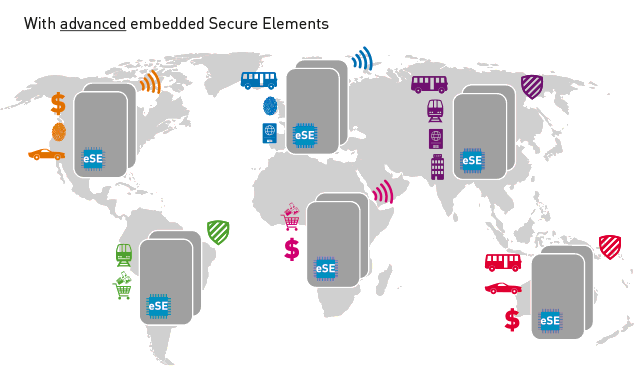
Embedded secure elements (eSE) are essential components of today’s smartphone design. Indeed, these tamper-proof chips ensure sensitive data is stored securely and access is granted only to authorized applications and people.
As the importance and number of use cases leveraging eSEs is constantly growing (e.g. micropayment, ticketing, biometry…), the decision of OEMs and device manufacturers to partner with a specific eSE provider is one that has become even more strategic and crucial for success.
To help make this decision process more informed, we’ve provided the criteria to consider when selecting a reliable and long-term eSE partner.
1. Which markets will the eSE allow you to target?
Every region and industry has its own specificities. For transport / transit ticketing, NXP’s MIFARE is a clear market leader worldwide, while Sony’s FeliCa is dominant mainly in Japan and Hong Kong. In the mobile payment sphere, EMV leads the race whilst MTPS is the undisputed leader in China.
Consequently, this atomicity of certification schemes constrains OEMs to design and maintain different handset reference design platforms to address every single market. OEMs can always adopt this strategy as long as the market is booming in order to gain markets share. However, with smartphone shipments growth slowing down, OEMs must streamline their device portfolio by reducing the number of reference designs. This helps then reduce the overall cost and realize greater economies of scale.
As a result of this, getting a single multi-applicative handset reference design platform able to address different markets is essential. Just imagine if you could get MIFARE and FeliCa for ticketing applications in a unique device platform, together with EMV and MTPS for mobile payment… With the arrival on the market of a ‘one size fits all’ eSE, such a dream could eventually become possible, a reality that Samsung endorsed as of 2017 for its latest Galaxy A, C and S8 device series.
2. What is the proven market acceptance of the eSE?
Reaching such a level of sophistication and getting complex eSE innovation squeezed into a single product challenges product reliability. It’s something we can’t ignore; once the product is embedded in millions of smartphones that are deployed around the world, smartphone vendors CANNOT suffer any product dysfunction/malfunctioning.
This demonstrates how a proven, undisputed and objective market acceptance becomes highly critical. The best way is to track which OEMs have already adopted such eSEs. Some OEMs are highly recognized for their high level of high standards when it comes to product compliancy checking. For example, Samsung is one of them, and working with them almost always means a de-facto accreditation. Even though this recognition is not everlasting, it demonstrates a high level of expertise and diligence from the eSE vendor.
3. How can the eSE contribute to a flexible vendor’s device lifecycle strategy?
First, in consumer devices markets, time-to-market is everything. Those who start first with the most advanced smartphone will likely grab a significant market share and enjoy high sales volumes.
Device makers have drastically modified their handset OS design and lifecycle to get this required flexibility. They now finalize device firmware once devices are already on the field via ad-hoc firmware patching management.
Embedded SE vendors must cope with this new stringent product lifecycle trend and develop post issuance administration capabilities. They must guarantee reliable remote embedded SE OS upgradeability / patchability in order to ensure device makers’ business continuity.
Secondly, with users expecting even sleeker, powerful and power efficient devices, OEMs need to save more space for new functions and improve smartphone design. Since March 2020, the embedded Secure Element can be combined with the eSIM function in a single security chip. This has been fast adopted by Samsung which has launched the world’s first smartphones, the Samsung Galaxy S20, Galaxy S20+ and Galaxy 20 Ultra featuring Thales’ embedded connected Secure Element.
In January 2021, this innovation has been selected as the winner of the “IoT Semiconductor Product of the Year” award in the the 5th annual IoT Breakthrough Awards program.
4. Which eSE-enabled services can device makers launch?
Embedded Secure Elements have numerous highly valuable security-related use cases:
- Mobile payment (transportation, ticketing, strong authentication…)
- Enterprise (email encryption & signature, VPN, data protection…)
- Device integrity (secure boot, secured IMEI, firmware upgrade and integrity…)
- Government (digital signature, eCitizen…)
- User protection (mobile ID, data encryption, access control…)
- Automotive (virtual car key…).
This wide range of applications often relies on different service providers worldwide, specialized for every region and application (e.g. banks, governments, car manufacturers, transport operators…). As a result, developing a portfolio of partners may look as a daunting task.
Ideally, device makers should be able to rely on a single point of engagement to many service providers across the world. Trusted Service Hubs have been specifically designed to provide this ‘plug once’ connection between service providers, handset vendors and mobile networks. It’s also a way to reach millions of new users to be equipped with new smartphones. For example, Samsung clearly identified this opportunity to provide an enhanced customer experience to its users by launching transport and ticketing services.
As a device maker or OEM/ODM, what’s your view here? Are there any other points you consider crucial for developing your business? Let us know your thoughts by tweeting to us at @ThalesDigiSec or leave comment below.


