Digitization offers Telecom Operators and OEMs an opportunity to rebuild their positioning, reimagine new business models, and create innovative offerings for customers. Customer enrolment and identity management represents significant milestones for this process. MNOs onboard customers in a diverse array of scenarios. Subscriptions and services can be conducted from multiple channels: through foot soldiers, telesales representatives, or in-branch customer representatives, or via digital channels without supervision.
In the current digital age, consumers are expecting to transact online in real-time. Instead of being restricted to business hours and fixed office locations, people can now quickly and easily apply for most services from the comfort of their own home at any time. Trusted Digital IDs helps MNO’s to deploy Omni channel strategy and play a fundamental role in digital transformation projects.
But whether customer onboarding takes place in person or remotely, the security and accuracy of the identity verification process needs to remain consistent. In addition, depending of national regulations and sensitivity of the services that can be accessed with the trusted digital identity, the process may vary. For example, in Germany is mandatory for Telecom Operators to identify their customers as mandated by Bundesnetzagentur. For prepaid cards, the identification must be done prior to the mobile service activation. The operator must identify the customer through a government-issued photo ID, and for remote identification a human interaction is envisaged (i.e. Videocall).
However, in the US and the UK, regulators in both countries take a fully risk-based approach in which they allow regulated entities to determine the best method to carry out identity verification depending on the level of risk that they are exposed to. Other countries such as India or Peru are using biometrics as method of verification. Different requirements, same approach.
How to create a trusted digital IDs in practice?
As defined in our previous post, a trusted digital ID consists of a set of verified attributes (like verified ID documents, biometrics, third party verification), thus providing a certifiable link between an individual and their digital identity. Consumer engagement begins with trust, and trust often begins with a trusted Digital Identity.
The creation process for a trusted digital ID generally includes the following 3 steps:
- Capture attributes as ID documents or biometric data
- Verify the authenticity of these documents and the identity of the person presenting the document by using biometrics or third-party checks
- finally digitize this digital IDs.

So how does it all work?
- Capture
Customer enrolment process may be different depending on the channel used by the consumer, to ensure the digitization of identities we must enable different solutions to capture end user identity attributesThe hardware needed can range from a smartphone, to specialized high-end scanners or tablets depending on requirements; The choice of hardware, of course, has implications for the level of quality and types of verification that can be conducted and ultimately for the level of accuracy of the results.
To begin, the subscriber’s information is captured including an identity document (passport, driver’s license, or national ID, resident permits etc.). In this process, information such as name, birth date etc. can be extracted through image analytics (optical character recognition). This technology enables accurate customer information and better populates customer databases. If required, we can also capture addresses from utility bills to complete the customer profile or enable further verification.
To enable a higher level of security, a biometric capture device (such as a mobile phone, web camera, tablet or specialized fingerprint scanner) is used to capture different types of biometrics including information from the face, fingerprint, handprint (palm), or iris.
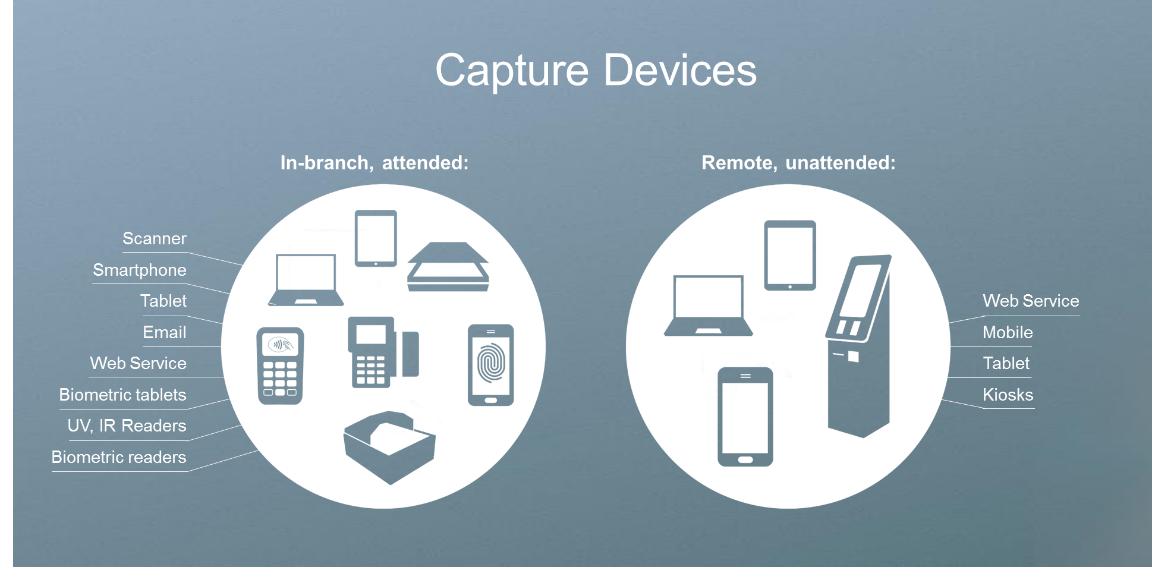
- Verify
Identity verification aims to verify the authenticity of the end user ID document and validates if the person is who they claim to be. This can be done using several solutions one can be required of a combination of them depending of the level of assurance.
Document Verification: Verifies authenticity of an ID document against a document template database. Implementing a document verification solution can be complex and may need adaptation to channel constraints, regulations and documents type. This involves online verification based on picture ID in visible light, advanced verification specialized full page scanners to verify embedded security features in white, infra-red and ultra violet light and electronic document verification for contact or contactless documents.
Verify biometrics: Telecom Operators are looking to leverage biometric technologies to strengthen security and to enhance user experience. For remote Identity Verification, biometrics enable a simplified user experience by reducing friction while also deterring fraud. It also provides a higher degree of personalization for the end users. Biometric technology is used to verify if the person presenting the document is who they claim to be but it also offers great opportunities for later identification to different services in a simple and modern manner. The two technologies most commonly used are facial recognition and fingerprint scan.
 Facial recognition: Facial features are identified through algorithms by extracting them from a good quality image of a face. One of these algorithms might use a selfie to analyze the relative size, positions, and/or structure of the eyes, nose, jaw and cheekbones. All of these features are then compare/contrasted with another image (perhaps an original ID picture) to see if there’s a match.
Facial recognition: Facial features are identified through algorithms by extracting them from a good quality image of a face. One of these algorithms might use a selfie to analyze the relative size, positions, and/or structure of the eyes, nose, jaw and cheekbones. All of these features are then compare/contrasted with another image (perhaps an original ID picture) to see if there’s a match.
 Fingerprint authentication: This refers to the automated method of verifying a match between two fingerprints. The analysis of fingerprints for matching purposes generally requires the comparison of several features of the print pattern. These include patterns, which are aggregate characteristics of ridges, and minutia points, which are unique features found within the patterns. This can be done locally by comparing the fingerprint with data on the chip or remotely with a third-party database.
Fingerprint authentication: This refers to the automated method of verifying a match between two fingerprints. The analysis of fingerprints for matching purposes generally requires the comparison of several features of the print pattern. These include patterns, which are aggregate characteristics of ridges, and minutia points, which are unique features found within the patterns. This can be done locally by comparing the fingerprint with data on the chip or remotely with a third-party database.
Third party checks: Identity verification can be improved using independent third-party data sources to validate and verify information that customers provide during onboarding. It is possible to verify identity information against authoritative sources such as a credit bureau, government data, active data Mobile Network Operators, watch lists and country sanction program list screening is also available.
- Digitalize ID
A digitalization process then links the personal information from the ID and connects it to the biometric information and other attributes. This cluster of data is saved as a digital ID, which can then be stored on an MNO’s premises or in a secure cloud-hosted database, depending on privacy regulations.
So, to recap, creating a Trusted Digital Identity takes three simple steps: ask the user to capture a picture of their government-issued ID and other attributes, take a selfie to make sure they are the same person on the ID, and then get a verification decision and create their digital ID!
The value begins with the customer’s experience and trusted digital ID makes it simple and convenient for the customer to access additional products and services, making it easier for the MNO to upsell. Going forward, trusted digital ID can be used to easily log in to the service. They’ll only need to present their biometric information, such as a fingerprint or face. This function enables users to more freely access the MNO’s services by lowering the authentication friction.


