This blog was written with my colleagues Brittany Jedrzejewski, Benoit Jouffrey and Jean-François Rubon.
In 2020, expectations for 5G have never been higher – it is clear users want the technology to provide a variety of new cases, while at the same time allow for some network customisation capability.
What’s more, exponential growth in both web and mobile traffic, especially for streaming video, and the explosion of connected devices mean that network infrastructures will need to scale effectively to deliver higher volumes of data, while remaining secure. Here we delve into a recent survey by Telecoms.com that depicts what industry leaders believe are the biggest 5G security challenges.
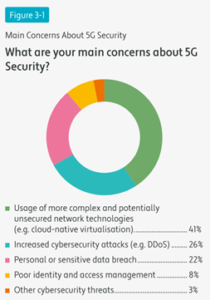
Ranking the Security Risks
As we may have expected, the survey uncovered that respondents were most concerned with the use of more complex and potentially unsecured network technologies that 5G will bring, with four in ten citing this as their main worry.
As the nature of the 5G core network is more flexible than any generation we have previously seen, we can use 5G in ways we previously could only do in a very limited case with 4G. Innovations such as slicing and cloud native virtualisation must therefore also be secured if the whole network is to be resilient to attack. As we haven’t had to secure these elements before, it is perhaps unsurprising that this is the primary concern of the respondents, especially if this then also puts consumers at a greater risk of a data breach. However, it is clear that with increased amounts of data processed –both at the core and the edge– more than ever before, there is strong need for data protection, at rest, in motion and at use.
On the other hand, those involved in the design and execution of 5G have learned lessons from previous generations of networks, for example 3G and 4G, and so have been able to better prepare the network for the more common attacks we have seen before, such as Denial-of-service attack (DDoS). This reflected in the number of respondents believing 5G will cause an increase in the number of such cyberthreats being significantly lower that the top concern.
Secure Equipment – the essential pillar
Garnering trust in 5G comes from ensuring that all the key equipment used in its deployment are also secure, as we must be able to create a chain of trust in the 5G networks.
This school of thought also appears to be reflected in the survey, with almost half the respondents stating that while their core network has the highest level of security trust, a variety of other components that will make 5G function at its most secure level, are also now essential to bolster trust in the security of the network as a whole.
With 5G, hardware security has never been more important. Tamper resistant components, such as 5G SIMs, contain secure elements that are essential in allowing secure 5G network access.
On the mobile network operator side, a trusted environment is maintained by their ability to securely and remotely swap, on-demand, the authentication algorithm contained in the SIM thanks to key rotation management. This gives them increased cyber resilience.
 For customers, 5G SIM cards allow for the full anonymisation of end-to-end subscriber identities thanks to onboard identity encryption. This eliminates the potential to misuse such information to locate and trace individuals or collect personal data. It also helps mobile operators to stick with increasing pressure about end-user’s data protection regulation.
For customers, 5G SIM cards allow for the full anonymisation of end-to-end subscriber identities thanks to onboard identity encryption. This eliminates the potential to misuse such information to locate and trace individuals or collect personal data. It also helps mobile operators to stick with increasing pressure about end-user’s data protection regulation.
Edge computing and Cloud security – the final step
With 5G we can deploy a new service called Multi-access Edge Computing (MEC) on a much larger scale than ever before.
MEC allows us to optimise the performance for ultra-low latency and high bandwidth services, as well as real-time access to radio network information that can be leveraged by applications.
By moving some of the computing capability out of the public cloud and closer to the end user and end devices, data doesn’t have to travel as far, which means it can be processed faster. For customers, moving computing, storage and management to the “edge” of the network will create faster speeds and near real-time decision-making. In practice this will bring high definition graphics, virtual reality, gaming and more to mobile devices.
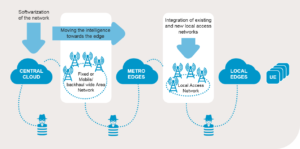
However, just as we need to secure the core network and the hardware associated with 5G, we must now also think about securing access networks between the core. Indeed, edge computing heightens the security risk because it involves distributing compute and storage processes away from one centralised location to a higher number of dispersed locations and endpoints, all of which must be secured.
As the survey rightly points out, end-to-end security is key here. With cloud-based security-as-a-service platforms, a diverse range of encryption, key management and hardware security module services are supported. From here, it is possible to route sensitive data to a guarded data centre on dedicated hardware, should it be deemed necessary. All of these features will help secure the data throughout the access network.
If we are to fully embrace the potential of 5G and other emerging digital services, we must first re-examine and re-architect how networks, applications and systems are delivered and secured. As the survey says, digital security specialists are one of the best placed entities to solve 5G security challenges, especially if we work in conjunction with mobile network operators.



