Hardware Security Modules (HSM) are vital to the security of today’s cloud-enabled, digital world. They act as trust anchors that protect encryption and the cryptographic infrastructure of the most security-conscious organizations in the world by securely managing, processing, and storing cryptographic keys. Without them, data, transactions and the increasing number of workloads in the cloud could not be protected.
That is why the largest cloud services providers – AWS, Google, IBM and Microsoft – now offer cloud HSM services to help companies keep data in their clouds protected. AWS was the first out of the block, followed by Google, then IBM and now Microsoft. Their expansion from storage and computing to more value added services like security is a natural extension of trying to capture more of their users IT spend.
Many Clouds, Many Workloads
While most companies are looking to run the majority of their IT workloads and applications in the cloud, most do not run all of them in one cloud provider. In fact, According to 451 Research, 69% of companies will have some type of multi-cloud/hybrid IT environment by 2019.
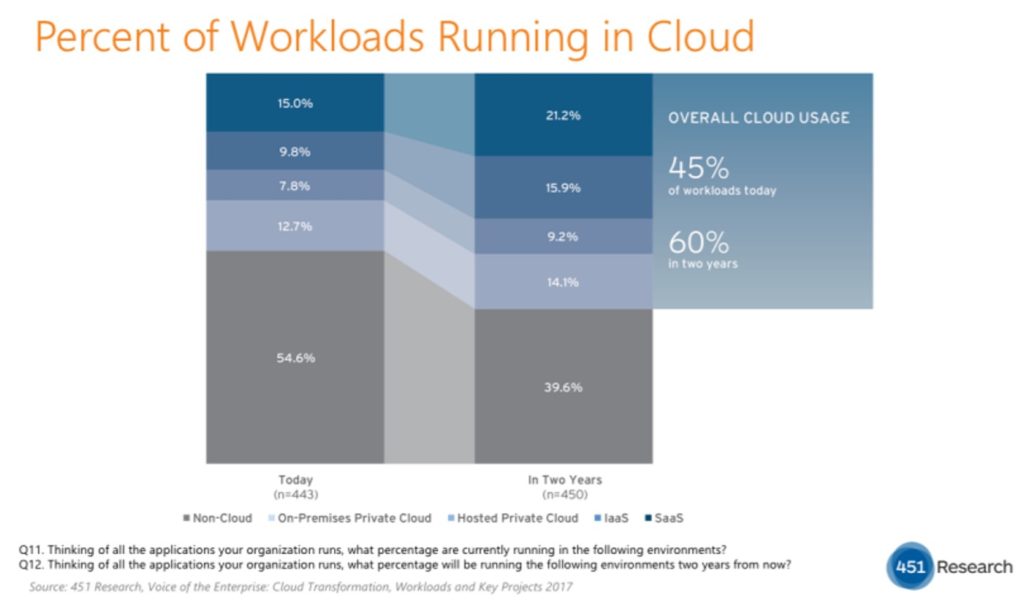
CRM, databases, storage, computing resources – each of these are often run from different cloud providers. In addition, many companies still have certain applications, data and workloads running on on-premises or private clouds. And while data and workloads are moving to the cloud, it does not by any means suggest that data and workloads stay in the cloud once they go there. Organizations also need the ability to pull workloads and data back from the cloud to on-premises or private cloud environments. In fact, a 451 Research survey found that 34% of respondents said they had moved their workloads from a public cloud to a private environment (cloud or otherwise).
What these data points tell us is that data and workloads move back and forth between private and public environments. It’s a fluid relationship. That means the hybrid, multi-cloud environment is more likely to be the norm as we move into 2019 and beyond. That means more complexity, which is problematic for securing data. So, if the cloud was supposed to make things simpler, that simply is not the case.
Islands of Encryption
If you are running sensitive applications and workloads in multiple clouds and they require encryption, your security policy or compliance mandates will probably require you to secure those keys in an HSM. And as noted above, most major cloud providers now offer a cloud HSM service. But how do you choose the right cloud HSM? Certainly your storage of customer financial data and PII in the Google Cloud will require you to use an HSM. And your application in Azure doing sensitive financial transactions will require an HSM. And yes, your blockhchain application in AWS will require an HSM.
But do you really want to manage each native cloud HSM in AWS, Azure, IBM or Google separately? Going this route creates islands of security, and each island (ahem, HSM provider) has different features and rules. In addition to the added costs of using different cloud HSM services, there are management and operational issues. For example, what if you want to move the keys between cloud HSMs when you move applications and workloads between clouds or back to a private environment? Wasn’t the cloud supposed to make things simpler?
There’s a saying among specialists in crypto. Amateurs talk about encryption. Professionals focus on key management. Having a centralized key management and crypto strategy is essential to the integrity of data, but current multi-cloud deployments run completely counter to this. Centralized key management and security relies on centralized equipment (in this case services), processes and procedures.
A Hybrid HSM Approach to Unite Them All
The smarter and simpler route is to use a cloud HSM provider that can centrally manage and secure your entire cryptographic operations across not just AWS, Google, IBM and Microsoft but also other cloud services such as Salesforce.com and Oracle as well as your on-premises applications. For many companies, the move to a cloud HSM needs to consider a more hybrid approach and be complemented by having on-premises solutions for when the cloud simply does not match with performance, operational or security requirements. That is why Gemalto has developed a new key management service as a complement to its existing on-premises solutions and create such a unique hybrid approach.
SafeNet Data Protection On Demand is a cloud-based platform that provides cloud HSM services as well as on-demand key management services through a simple online marketplace. Through our cloud-based HSM on Demand, Gemalto helps security teams and service providers deploy a centralized key and crypto management infrastructure for developers or end users working in any cloud. With an agnostic cloud HSM platform offering complemented by compatible on-premises offerings, security teams benefit from increased operational efficiencies to manage and secure keys across all cloud services using the most appropriate hybrid platform. From a features and capabilities standpoint, users get all of the benefits of the market-leading SafeNet Luna HSM but with the cost and operational benefits of a cloud-based service. Cloud HSM On Demand can be used for a wide range of applications and use cases including digital signing, securing PKI, generating and securing CyberArk keys, protecting Oracle TDE encryption keys, and securing your Hyperledger framework and blockchain Hyperledger artifacts – just to name a few.
Take a look at SafeNet Data Protection On Demand and get started with a free 30-day evaluation. Also, watch our webinar, Choosing the Right Cloud HSM.


