
5G Stand Alone (5G SA), the most recent generation of mobile networks, is a rapidly accelerating alternative to its 4G and 5G Non-Standalone (NSA) predecessors. With around 60 networks already live worldwide and another 83 planned for launch, we are seeing a significant adoption of this advanced technology.
Unlike the first generation 5G network (NSA) which was merely an extension of 4G infrastructure, 5G SA operates on a fully autonomous architecture. This delivers a host of benefits for end users. From lower latency and battery drain to greater connectivity, capacity, reliability and speed, this next-generation network certainly represents a step up in terms of performance. But it’s the unparalleled user privacy protection and security that truly sets it apart, with its data anonymisation capabilities ensuring user identifiers don’t end up in the wrong hands.
However, the anonymity of users can pose a significant challenge for Law Enforcement Authorities (LEAs) who often need to intercept mobile networks as part of criminal investigations. Let’s first look at what digital identifiers are at stake, and how mobile operators can balance the risk of cybercriminal interception of data with the need to enable lawful interception…
5G NSA Interception: Open to (almost) anybody
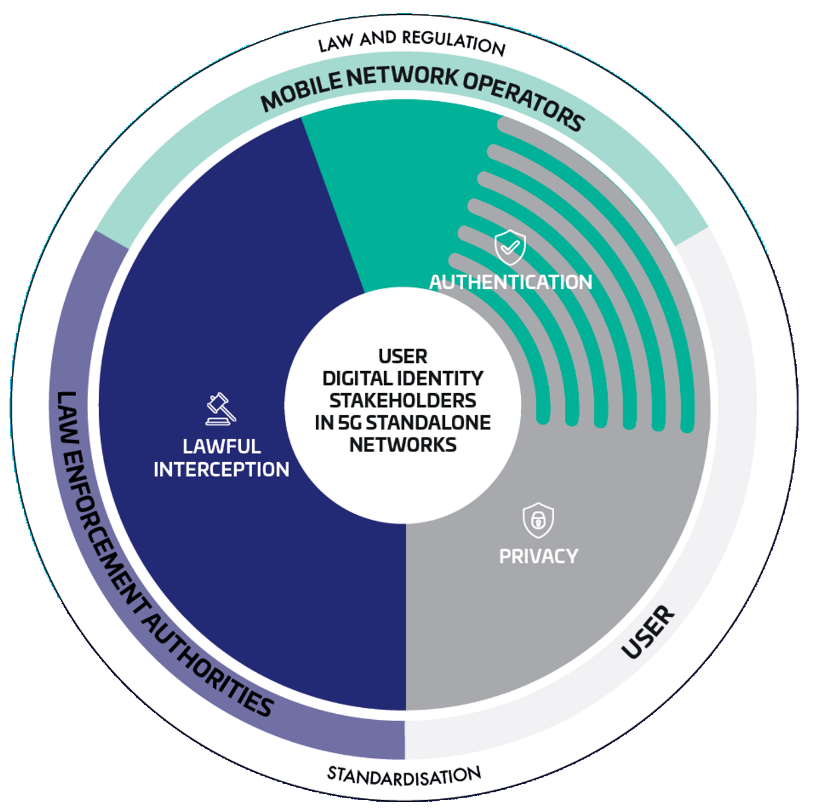
All SIM cards have a form of digital identity known as either an ‘International Mobile Subscriber Identity’ or ‘IMSI’, or ‘Subscription Permanent Identifier’ or ‘SUPI’, issued by the mobile network operator (MNO). This acts as an identifier so the carrier can authenticate their users for network access purposes.
The IMSI/SUPI data transmission from the user to the MNO across 5G NSA networks is formatted in clear text – i.e. it is not encrypted. While this makes said data easily readable for the MNO at the other end, the networks can also be easily intercepted – whether it be for good or bad intent.
Hackers, on the one hand, may attempt to do so to launch cyberattacks. For example, bad actors may leverage an illegal IMSI catcher—a device that impersonates a legitimate network to intercept user identifiers. Locating users, intercepting communications, and even conducting fraudulent activities such as phishing scams, data theft, and surveillance are just some potential outcomes.
Law Enforcement Authorities like the Police, on the other hand, will often require access to the digital identities in mobile communications as an essential part of criminal investigations. This lawful interception centres around preventing and investigating crimes and ensuring public safety, whether it be for search and rescue purposes, suspicious call interception, suspect identification, or fraud and terrorism prevention.
5G SA: The Anonymity Differentiator
Where 5G SA differentiates itself from 5G NSA is in its ability to anonymise said user data, creating a siloed access so that identifier information is only accessible to the MNO in question. This enhances user privacy and trust in a context of increasingly widespread cyberattacks targeting mobile networks.
To address these vulnerabilities, 5G SA incorporates robust privacy concealment mechanisms. The SUPI is encrypted into a ‘Subscriber Concealed Identifier’ (SUCI) before transmission, to avoid sending the plain SUPI across the network. This privacy concealment can be performed either by the 5G SIM/eSIM card or by compatible 5G SA devices, and by the HSM (Hardware Security Module) in the User Data Management system.
The SUPI anonymisation effectively renders IMSI catchers ineffective, ensuring that the permanent identifier remains concealed from any unauthorised interceptors. Once safety transmitted, only MNOs can decrypt the SUCI.
The Middle Ground: Facilitating LEAs
But with LEAs now cut off from this essential intel by default, how can MNOs offering 5G SA networks maintain these user privacy protections while delivering on their lawful interception obligations to LEAs?
To address this challenge, 5G identification association was introduced to help LEAs ‘reidentify’ SUCIs. This enables LEAs to retrieve real-time permanent user identifiers on demand under specific circumstances. However, by only providing very specific access allowances for legitimate use cases, MNOs and users alike can still rest assured that mobile users’ digital identities remain concealed from malicious actors.
Conclusion 
The digital identity of mobile users has always been a critical concern for MNOs and LEAs. With users exposed to significant privacy risks across legacy 4G and 5G NSA networks, the 5G identity association for 5G SA effectively strikes a balance between protecting users’ privacy and ensuring that LEAs can continue their critical work. As 5G SA networks continue to expand globally, this approach will be a key enabler to ensure that ‘win win’ outcome for all mobile connectivity stakeholders.
To find out more, download our white paper here.



