Posted on 01 February 2018 by Lorna Ayoun-Berdugo
Learn how cloud access management can provide confidence in your data security. By customizing and adapting access policies to various scenarios, IT can ensure that policies are as strict or lax as required—prompting for no credentials, a single credential or multiple credentials when a user logs into an SSO session.
Posted on 12 December 2017 by Lorna Ayoun-Berdugo
Identity and Access Management (IAM) is the security discipline that enables the right individuals to access the right resources at the right times for the right reasons. IAM solutions provide a methodic framework for granting and requesting access to applications along with enforcing access controls and ensuring visibility into access events.
Posted on 02 November 2017 by Lorna Ayoun-Berdugo
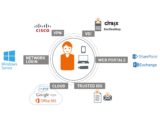
How do you implement a cloud access management solution? Cloud apps in the enterprise have become mainstream, but moving to cloud-based applications can be challenging. There’s way for you to streamline cloud adoption for everyone, follow these 4 easy steps.
Posted on 26 September 2017 by Lorna Ayoun-Berdugo
Starting in Feb 2018, all who access systems that hold credit card data will be required to authenticate with multi-factor authentication. This is a direct outcome of PCI DSS’s new requirement providing best practices for organizations that need to extend their MFA and comply.
Posted on 05 August 2017 by Lorna Ayoun-Berdugo
PCI DSS 3.2 standard has been updated, are you in compliance with Requirement 8? Multi-factor authentication is one of the biggest changes – whether in office, or accessing systems remotely. Learn more about how to comply with PCI with multi-factor authentication.
Posted on 07 June 2017 by Lorna Ayoun-Berdugo
Why do we need access management? With data breaches at an all-time high, keeping employees and data safe is challenging for IT. An access management solution is beneficial for users and IT. Learn how access management solves enterprise access issues.