44 zettabytes of digital data are anticipated by the year 2020. To put that into perspective, that’s 44,000,000,000,000,000,000,000 bytes of data expected to be produced by the year 2020, according to IDC predictions. So it doesn’t seem far-fetched to presume that securing this data is going to be a top priority for consumers and enterprises alike. But if there was a hint of doubt in people’s minds, this latest report from Gartner should set the record straight. The study identifies the top 10 IoT technologies for 2017 and 2018 – and guess what? IoT Security is listed right up there! It’s no wonder that the GSMA published its own set of IoT Security Guidelines earlier this year.
The Complexity of IoT Security
IoT brings so many disparate players to the market that it often becomes difficult to formulate a holistic view on how to secure it. The diversity and complexity of these connected ecosystems often leads organizations to brush the IoT Security topic under the carpet. Should a device manufacturer (OEM) be concerned about securing its device alone, or make efforts to secure the ecosystem it’s going to be a part of? Should the cloud service provider be concerned about securing its cloud infrastructure alone, or the devices that are going to be connected to its infrastructure as well?
When a CIO or CTO faces these questions, or questions about which technology to use for their connected systems, the subject can seem so daunting that the topic just drops off the radar. But this is where the Gartner report comes in handy – it’s a much-needed wake-up call to signal that these issues need to be discussed urgently. The issue needs to be discussed now; in your next technology summit, your next board meeting or your next team briefing. It cannot be put off for later.
Simplifying IoT Security
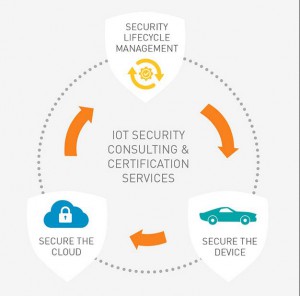
This is why we recommend taking a step back and simplifying the implementation process for IoT security. Getting too bogged down with technology can be overwhelming. Seeking help from experts in digital security is not an indication of weakness or lack of competence. Our recently published e-book on IoT security provides a framework that helps you take that step back, look at the big picture and visualize IoT security’s three core areas in the context of your project: securing the device, securing the cloud, and securing lifecycle management.
Companies no longer need to “fear” IoT Security – instead they should embrace it as an enabler that’ll drive their business into the future.
If you’re keen to learn more about IoT security, why not speak to us at iot.query@gemalto.com?Alternatively, if you want to share your perspective on IoT security, let us know by tweeting at @Gemalto or by posting a comment below.