
In a previous blog, we explored how businesses are increasingly moving towards a Zero Trust mindset when adopting cybersecurity practices. The very essence of Zero Trust, as the term implies, is to assume the stance of distrust towards any user or device that tries to enter the corporate environment – it follows the mantra of “never trust, always verify”.
While Zero Trust is an important principle, it’s just a mindset shift that reflects the acknowledgement of new threat vectors arising from an increasingly stretched corporate environment. Mindset changes like this need to be accompanied by a pragmatic approach to security implementation, which is where Security By Design comes in.
Security By Design
Making sure that software and hardware systems are secure from the ground up – from the genesis of design to deployment – has never been more important in our connected world. With the explosion in the volume of workplace devices and cloud environment systems, going to the source or root of each component, whether that be hardware, software or data, is increasingly critical. With these systems needing to move, store and provide access to sensitive data, they are prime targets for a cyber-attack – making a branch and root approach to cybersecurity all the more important.
Security by design is an approach to software and hardware development that seeks to make systems as free of vulnerabilities and impervious to attack as possible through measures such as continuous testing, authentication safeguards and adherence to best programming practices. Building security into products from the start of their development addresses the all-too-common tendency for security to be an afterthought, with designers patching security holes as and when they are found.
Without ensuring every aspect of a system has the highest level of security from the point it is created, there is a higher risk that the device or system can be hacked. It is therefore essential that manufactures or engineers are building secure products to create a strong bond of trust between developers and users. If it becomes apparent that the software or hardware of a device has been compromised by a malicious attack, this bond of trust is broken, turning consumers away from advances in technology, such as products that use cloud applications, and hindering further innovation.
To be truly secure, sensitive source code and data must also rely on a hardware root of trust like a Hardware Security Module (HSM) to ensure that it is encrypted, that any sensitive data remains confidential, and that its integrity can be guaranteed. This frame of mind, combining secure hardware with a ground-up approach to processes, is essential for good quality cybersecurity practices.
Zero Trust by Design
Over the last few years, we’ve seen enterprises increasingly shift their workload to the cloud, propelled by the use of applications like Salesforce, Box and Office 365. This has accordingly required a change in attitudes to information and cybersecurity to keep up with this evolving workplace.
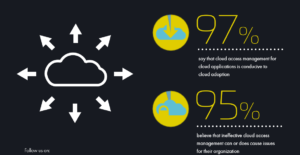
The security threats that accompany the evolution of the cloud pose a daunting prospect for IT departments, as the rise in the number of cloud environments involves an expanding number of untrusted endpoints. Indeed, 49% of business believe cloud applications are the biggest targets for cyberattacks.
One of the ways to address these threats is to apply the principle of Zero Trust to the foundational concept of Security by Design. Accordingly, this makes sure security is rooted in every product and service by design and that a company does not trust anyone by default, even those already inside the network perimeter.
Since the technical maturity of organizations varies significantly, it’s challenging to define a standard approach to Zero Trust By Design. Ultimately, each company needs to make a self-assessment of its capabilities and the spread of its sensitive data to determine which methods and tools are the most appropriate to protect cloud and web-based apps, while ensuring these security measures provide are as frictionless as possible.
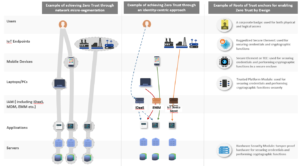
In some cases, it may be appropriate to implement a tightly regulated internal infrastructure, where even the web browser is limited to a single brand and hardware-based tokens, which use private firmware would ensure security is almost impenetrable. Yet, for other companies, this sort of tightly regulated IT infrastructure could cause friction for users.
Achieving this balance, between a high security environment and user convenience, is the constant compromise that CIOs and CISOs need to strike. In order to do this, businesses require flexible security solutions that are resilient and built for a multi and hybrid-cloud environment. By effectively walking this tightrope, organisations can achieve a Zero Trust By Design information security approach that satisfies both cyber diligence and user experience requirements.
To learn more about how Thales’ IDaaS solutions enable secure, convenient access to numerous cloud applications, or for help on how to choose the right option for your organization’s cybersecurity and make your CISO’s life easier, visit our website https://safenet.gemalto.com/cloud-data-security/.
In addition, for an even more in-depth review, you can also take a look at the whitepaper by Identity Defined Security Alliance on role of identity for implementing Zero Trust.


