In a previous blog, I discussed why risk management services should be combined with document verification and facial recognition to enhance the digital onboarding process. But that is just the start of the customer journey.
Once your new customer has signed up, they will be able to access their accounts online at their convenience and make transactions quickly and securely. Having a good multi-factor authentication solution in place is vital, which is something we have advocated for decades. Nowadays customers have come to expect that a second factor is added when accessing their online bank account, be it a fingerprint or face recognition authentication on a mobile app, an OTP token or another solution.
Customers trust their financial institution to keep their account secure, but at the same time they want a frictionless experience. While new stricter regulations, such as PSD2 in the EU, are putting high pressure on financial institutions to introduce Strong Customer Authentication (SCA), they also focus on user experience and thus allow exemptions when the risk level is low.
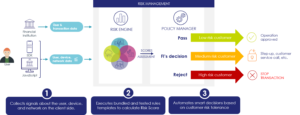
And this is where risk management comes into play to enhance user access. By adding smart risk management services to the access phase, the risk level of every single customer transaction is analysed and a recommendation on the most appropriate authentication method is given. This can help mitigate account takeover (ATO) fraud and with risk-based authentication (RBA) you can define continuously adaptive policies based on customer segmentation, customer preferences and use cases. These RBA authentication techniques are running silently in the background to provide the best end user experience.
Risk based authentication
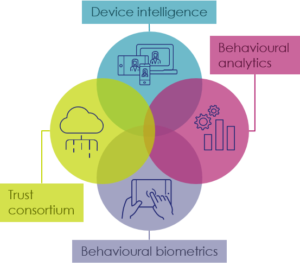
Let’s have a look at the risk management techniques that can be used to recognise your good users:
- Device intelligence allows you to accurately identify recurring devices, detect high-risk networks and locations and spot device anomalies which can indicate fraudulent activity.
- Behavioural biometrics looks at inherent user behaviour and analyses how someone types, moves their mouse or holds their device to create an individual profile. The profile is used for future sessions to detect account takeover or social engineering fraud, since typing pattern usually differ when a fraudster is coaching a victim to make a transaction.
- Behavioural analytics analyse user habits at individual and population level to detect unusual behaviour. For instance, it checks what time of day the user access bank services, from which location and which device, or if any out of ordinary transactions occur.
- Trust consortium evaluates billions of events to help you know who to trust, even if they are new to you, by gathering anonymised and encrypted insights from online events across our clients. If an IP or device ID is linked to past fraud a warning will be issued.
Risk management techniques
Collecting all this information from several different sources and integrating them into your authentication process can be difficult. For this purpose, a Policy Manager is needed that can combine all incoming data into one global risk score and decide the next course of action; allow the transaction if the risk is low, challenge with an additional layer of authentication when a risk has been identified, or block if the risk is deemed too high. This way the authentication flow can be orchestrated in a flexible and dynamic way, making it harder for fraudsters to predict and plan an attack. The step-up challenge can vary depending on which multi-factor authentication options the financial institution has implemented, be it FaceID or fingerprint on mobile, or a dedicated hardware device to generate one-time passwords (OTP).
Preventing fraud is of course top priority, but equally important is the user convenience you provide by adding risk management. The objective is to differentiate between users who pose a risk, and the vast majority that do not. The customers who do not pose a risk should have a frictionless experience when accessing their account and not be bothered with unnecessary cumbersome authentication steps.
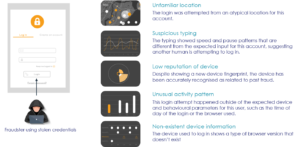
Detecting account takeover
We strongly recommend that you take a holistic view, a risk management solution should be used both for onboarding new customers as well as to protect them while they access and use your services online. Click here to learn how we can help you secure and enhance onboarding and access to your digital banking services, or contact us directly with your questions.