Looking back at how financial institutions (FIs) have been protecting access to their remote digital services can help us to understand the banking authentication technology used today, and what may evolve in the coming future. But before we can get to what’s coming, we need to start from the beginning.
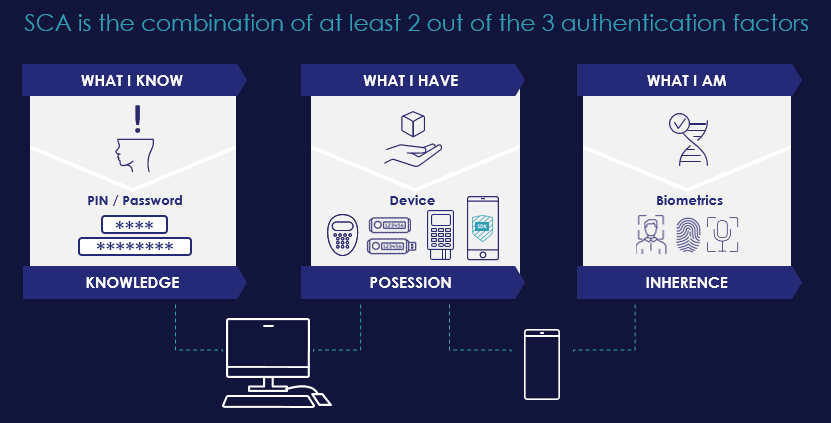
What is Multi-Factor Authentication?
Service providers (banking or otherwise) need to have assurance about the identity of the user attempting to access their services. To do so they have three options:
- Request the user to present a secret that only he/she is supposed to know, like a password, a PIN, or the answer to a security question. This is referred to as a Knowledge Factor.
- Request the user to prove that he/she is in possession of a physical device that only the user should have, for instance, a banking card, a grid card, a token or a phone. This is referred to as a Possession Factor.
- The final option is biometrics, the Inherence factor.
Any one of these authentication factors alone is hardly proof of identity, as someone can take my device or find out my password or even capture my biometrics.
However, the banking industry (among others) have agreed that presenting at least 2 of those 3 independent authentication factors is good enough proof of a user´s identity to grant access for most use cases. This is what the industry calls Strong Customer Authentication (SCA), also commonly referred to as Multi-Factor Authentication (MFA).
Read more about strong customer authentication
The evolution of remote financial services
If we look back at the evolution of access to remote financial services over the past 25 years, we can safely say that innovation and advancements have been driven by the need to improve security and user experience (UX) – two things that can sometimes find themselves at odds with each other.
In the late 80s and early 90s, banks started to offer remote digital services (commonly referred to as e-banking) to their users which required only a username and password. This represented the first major downgrade of security. Up until this point, the only other unattended service that banks were offering was the use of ATM machines, where users authenticate through a token (banking card) and a PIN – i.e. two factor authentication.
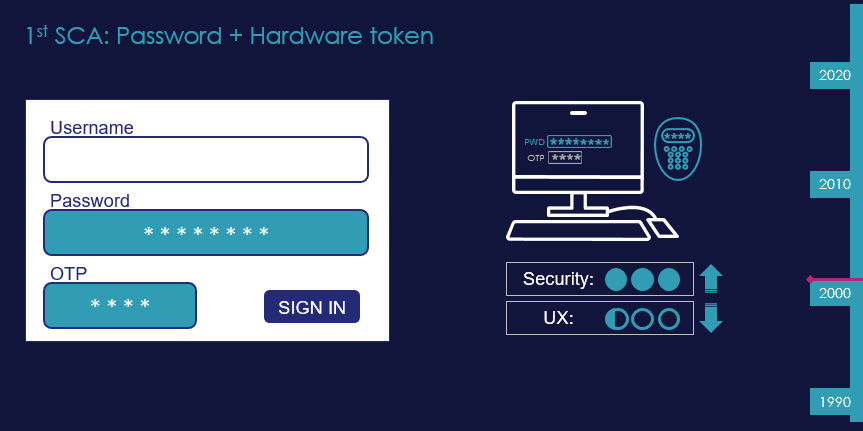
Introduction of One Time Password tokens
The weakness of username and password was evident and unsustainable for remote banking services, and so by the mid-90s, financial institutions (FI) begun to introduce possession factor. Probably the first and most rudimentary form of possession factor were grid-cards, shortly followed by much more robust, friendly, (and more costly) One Time Password (OTP) tokens. l pieces of tamperproof hardware with a display that, at a push of a button, generated a unique PIN for every authentication attempt. The user would log in to the e-banking service by entering their username and password, plus an OTP extracted from the device. This OTP was then verified by the bank´s authentication server and would serve as proof of possession of the token.
We can see here how the threat of fraud (and brand damage) drove banks to introduce SCA, which greatly reinforced security at the expense of user experience. Less fraud for the banks – more pain for the user.
The rise of the mobile phone
Around the turn of the century, almost everyone, or at least almost everyone with a bank account, carried a mobile phone in their pocket. It quickly became tempting for banks to rely on the user´s own mobile phone as the possession factor. Thus SMS OTP came into the picture. In this case, the user would present a password as a first factor, before receiving an SMS from the bank with an OTP to be entered on the login portal as possession factor.
Compared with the use of a dedicated tamperproof hardware token, using password and SMS OTP can still be considered SCA, but represents a clear downgrade of security. But most FI´s gladly accepted this in favour of better UX for the end user, lower cost, and ease of deployment.
But things didn’t stop there. Before long, feature phones were a thing of the past, and smartphones were the future – bringing with them what we now know as the digital banking revolution.
Look out for my next blog post where I explore the solutions and technology behind the digital banking we know and use today, and what we can expect to see in the not so far future.
For further reading, visit:
-
- The Evolution of Digital Banking Authentication – Part 2 – The Digital Banking Revolution
- The Evolution of Digital Banking Authentication – Part 3 – FIDO and Passkeys will rock the digital world
- The Evolution of Digital Banking Authentication – Part 4 – Passkeys: The future of digital banking authentication
- How our payment habits are changing: three major trends that are here to stay
- Deploying a Modern Card Program



