In my previous blog posts I took you through the last 30 years of digital banking security and how it has evolved to what we know and use today. In my cliff hanger I mentioned FIDO and passkeys and how they will change the landscape – it’s time to dig deeper and discover how this technology will mark a new era for Strong Customer Authentication (SCA).
FIDO Alliance
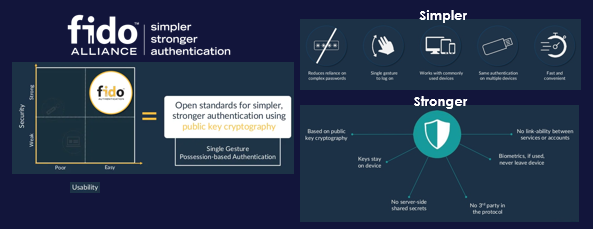
In 2013 FIDO Alliance was founded as an open industry organisation with a very focused mission: to build authentication standards to help reduce the world’s over-reliance on passwords. To do so, FIDO Alliance has released a set of new specifications and protocols for SCA based on the combination of biometrics as the first factor, and possession as the second factor. In short, no knowledge factor and no passwords.
FIDO Strong Customer Authentication
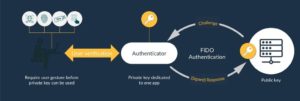
What FIDO Alliance does, for a given user and service, is generate an authenticator consisting on a cryptographic key pair, on-board a FIDO enabled device; the private key, remains on the device , while the other key is sent to the service provider’s FIDO Authentication Server. Once an authenticator has been generated and registered, it can be used to securely authenticate the user on that device. The user will then present biometrics that are checked locally on the device and upon successful validation of biometrics, it will trigger the cryptographic exchange between the device and the authentication server to validate the device.
Read more about strong customer authentication SCA
FIDO native support on devices

An impressive list of companies have joined FIDO Alliance over time, including chip makers, computer and smartphone manufacturers, payment schemes and banks. But, most importantly, Microsoft, Apple and Google all joined and pledged to support FIDO at OS level on Windows, Mac OS, Android and iOS. That pretty much grants native FIDO support to all laptops, PC computers, tablets and smartphones.
With that level of ubiquity and underlying “plumbing”, FIDO have big chances to succeed in becoming the next mainstream SCA technology. As of January 2022, according to FIDO Alliance, more than 4 billion commercial devices with native support for FIDO, were already deployed worldwide. That is a big deal as OATH has been the dominant standard for strong customer authentication for 30 years, and we never enjoyed native support for it on PCs, laptops or phones.
What is WebAuthn?
FIDO Alliance have gone one step further – they reached out to W3C, the standards body for all things internet, and worked together to define a new standard API, published by W3C under the name of WebAuthn. As its name hints, the purpose of WebAuthn is to enable any web service to call the OS of the device where it is running to request FIDO based authentication. Never before has it been possible for web services to directly integrate strong customer authentication – the best we could do was initiate an out-of -band push from the web service to a mobile app in the user´s smartphone, where we could have SCA implemented via an SDK. Now, with WebAuthn, a user with a FIDO enabled laptop and a WebAuthn enabled browser, can register, store and use a FIDO authenticator for that service on that device, with a user experience as sleek as simply presenting biometrics on the device. WebAuthn was published by W3C in 2018 and is today supported by all major web browsers, including Microsoft Edge, Google Chrome, Apple Safari and Mozilla Firefox.
FIDO is everywhere
So, in summary, as of January 2022, current OS versions used by every single smartphone, tablet, PC and laptop are already FIDO enabled – and every major browser is also ready to use FIDO thanks to WebAuthn.

Now, if only service providers and end users would know about it …
The future is passkeys

On May 5, 2022, Apple, Google and Microsoft issued a joint PR what appears to be a first, and the only joint PR I can find on record. This PR, in essence, is a very strong pledge to kill passwords.
The first paragraph sums it all up:
“In a joint effort to make the web more secure and usable for all, Apple, Google, and Microsoft today announced plans to expand support for a common passwordless sign-in standard created by the FIDO Alliance and the World Wide Web Consortium. The new capability will allow websites and apps to offer consistent, secure, and easy passwordless sign-ins to consumers across devices and platforms”
They also gave a name to the technology for end users to refer to moving forward, “passkeys”.
The media impact of the announcement was immediate, with lots of articles and commentaries. In the weeks that followed, Google & Apple unveiled their specific plans for passkeys during their annual developer’s conferences: Google I/O and Apple WWDC. Apple announced that passkeys would be deployed commercially on iOS 16 and Mac OS Ventura, set for release after the summer. Google and Microsoft also deployed resources for developers that enable them to start building passkeys to support web services.
What can we expect next for authentication?
So we have a name, we have documentation for developers to do the work and we have all the OS and browser support we need. Now it’s just a matter of time before we begin to see services supporting passkeys more and more. Users are going to love it. Service providers, including financial institutions are going to love it… There is not a single cloud in the sky… or?
In my next blog post, I will look in detail at passkeys, how they differ from FIDO Authenticators as we knew them, their unique benefits, and the unique concerns they raise to some FIs.
I will also speak on this topic at the FIDO authenticate conference in Seattle on October 18.
For further reading, visit:
- The Evolution of Digital Banking Authentication – Part 1
- The Evolution of Digital Banking Authentication – Part 2 – The Digital Banking Revolution
- The Evolution of Digital Banking Authentication – Part 4 – Passkeys: The future of digital banking authentication
- How our payment habits are changing: three major trends that are here to stay
- Authentication cloud services to secure access to digital banking



