We’ve talked quite a bit recently about what it  means to unshare your sensitive data and deploy encryption as an IT service to unify data protection company wide.
means to unshare your sensitive data and deploy encryption as an IT service to unify data protection company wide.
If you’ve found yourself nodding in agreement as you’ve read these posts, good. The threats to your data aren’t going away. In fact, they continue to grow – just like the volume of data that you need to protect. It’s time to move beyond strategy and get to work.
But for those of you responsible for keeping corporate data assets safe, finding the best solution can be a daunting task. You likely have structured and unstructured data to protect at every layer of the technology stack, as well as data flowing across your network and between data centers. And speaking of data centers, you likely need to protect data on premises, as well as across multiple cloud and virtual environments.
You have so many choices to choose from, so where to you get started?
Locate Your Data Across All Environments and Pinpoint a Solution
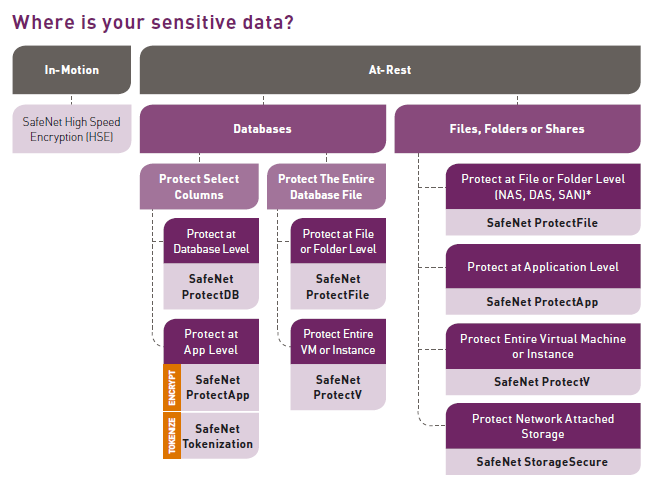
To get started, consider where your sensitive data can be found across all of your on-premises, cloud, virtual, hybrid, and big data environments:
- Data at Rest – Sensitive data is moving to or through any of the following places: application and web servers, file servers, databases, and storage
- Data in Motion – Sensitive data is flowing across your network and/or between data centers
Then follow our simple, step-by-step guide to map your needs to the appropriate data protection solution.
Protecting Data in Motion
As more sensitive assets traverse networks from site to site and across data centers, on-premises, and in private and public clouds, organizations need to know that their data in motion is secure, especially in multi-tenant, geographically distributed environments. The availability of greater bandwidth allows us to exchange information faster and more frequently, but the huge growth of often sensitive data volumes transmitted across networks presents real risks.
If you have sensitive data in motion, including real-time voice and video streams, as well as metadata that needs protecting, high speed encryption is the best option for you.
Protecting Data at Rest
If you have sensitive data at rest, it will typically reside in either a database or in files, folders, and shares. There are a number of options for applying protection to this data, and each of the solutions should be deployed with an enterprise key manager for centralized key and policy management.
If the data resides in a database, you have two options for protecting it:
- Option 1: Protect select columns in the database
Apply column-level encryption, application-level encryption, or application-level tokenization if you have sensitive data that resides within specific fields of a database, such as credit card numbers, social security numbers, email addresses, etc. - Option 2: Protect the entire database file
Apply file system-level encryption, transparent data encryption (TDE), or encrypt the entire virtual machine or instance if you have database exports, archives, and backups that contain sensitive information.
If you have sensitive data located in files, folders, or shares in on-premises, you have four options for protecting it:
- Option 1: Protect data at the file-system level
Apply transparent and automated file-system level encryption of server data-at-rest in the distributed enterprise, including Direct Attached Storage (DAS), Storage Area Network (SAN), and Network Attached Storage (NAS) servers using CIFS/NFS file sharing protocols. - Option 2: Protect data at the application-level
Apply protection at the application-level by encrypting select files and folders before they are stored on the file server. - Option 3: Protect data at the remote folder-level
Apply protection to NAS folders on shares on remote storage with the granularity necessary to encrypt select, sensitive folders, not entire storage arrays. - Option 4: Protect the entire virtual machine or instance
If you have large quantities of sensitive data to secure in a public cloud environment as a result of migrating your data center to the cloud, running a hybrid cloud environment, or bursting to a public cloud when applications running in a private cloud or data center need additional compute power, apply protection to the entire virtual machine or instance.
Ready to get started? For more information and to learn more about Gemalto’s portfolio of SafeNet data protection solutions, download the new guidebook, Protect Your Sensitive Data: A Step-by-Step Guide to Finding the Right SafeNet Data Protection Solution for Your Organization.


