A Practical Guide to Public Key Infrastructure
We’ve blogged frequently about various topics around Public Key Infrastructure (PKI), but it’s also beneficial to have a refresher from time to time. One of the benefits of talking to IT professionals is you get to hear about their needs, from compliance requirements to employee convenience concerns. Let’s take a quick look at PKI and how it can be the right security fit for the enterprise ecosystem.
What is PKI?
PKI is a well-known security ecosystem used by top enterprises, defense departments and governments around the world. Regulations, increased use of cloud-based services and the Internet of Things (IoT) are prompting a recent surge in PKI adoption. One of the top cited reasons for enterprises to select PKI is compliance. Regulations such as GDPR, PCI DSS, DFARS, and eIDAS (please click on each for our infographics) are calling for authentication, data protection and physical access controls.
PKI supports the distribution and identification of public digital certificates. It is a collection of hardware, software, and processes that support the use of public key cryptography and the means to verify the authenticity of public keys. PKI enables users and computers to verify the identity of parties they’re communicating with, and securely exchange data over private networks as well as public networks such as the Internet.
With the assurance of identities, the concept is similar to a secret handshake. Users may exchange an envelope with a message written in code; but with PKI, both parties can be certain the person they’re exchanging with is truly who they say they are. That assurance of identity comes in the form of a digital certificate from a certificate authority (CA).
Components of PKI
1. Digital certificates—a form of identification, much like a driver’s license or passport, only in electronic form. X.509 is a standard certificate for PKI and defines the different information you could find on the certificate, such as information about the identity of the owner, as well as other data such as serial number, issuer name, validity period, public key algorithms, and much more. A digital certificate must be issued by a certificate authority that ultimately guarantees the validity of the information in the certificate. The digital certificate is what pairs the key to a person’s identity and what guarantees you can trust the sender is who he claims to be.
2. Cryptographic keys—a string of bits used by a cryptographic algorithm to transform plain text into cipher text or vice versa. Public and Private keys are each comprised of a long string of random numbers and alphabetic characters. The public key can be shared, but the private key is known only to the owner. The public and private key pair is mathematically related, so data encrypted with a public key may only be decrypted by its corresponding private key and vice versa.
How Key Exchange works
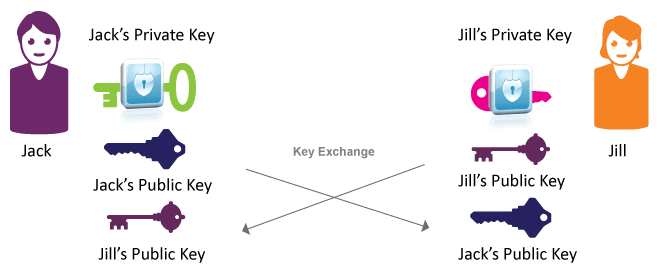
We can’t stress enough how vital it is to protect the private keys!
3. Smart cards—the private key is the most sensitive data in computer security and must be stored in a place where no one will have access, and in such way that if someone tries to steal or use our private key without our consent we’ll know about it (tamper proof and tamper evident). A smart card is an electronic integrated circuit, a microprocessor (a chip) that is designed to store cryptographic keys and preform cryptographic mathematical operations in a secure and efficient way.
4. Certificate Authority (CA)—a trusted entity that generates digital certificates. We must trust the CA to verify the person’s identity before issuing a digital certificate. In many ways, this is similar to a passport or driver’s license (used as ID), but the trusted party there is the government. The CA responsibilities include issuing certificates for intended identified owners, providing attributes in a certificate and verifying them, managing which certificates were issued, when they were issued, and who holds them, and issuing and publishing the certificate revocation lists (CRLs), to which revoked certificates are added.
5. Key security—a Hardware Security Module (HSM) is a FIPS certified dedicated hardware device, which is separately managed and stored outside of the operating system software. It comes with multiple tamper-resistant and self-destructing features in case there’s an evidence of continuous attacks. The best security practice is to store the keys of CAs in an HSM.
6. Management tools—Credential Management Systems (CMS) are critical for the day-to-day operations of a PKI environment. CMS software automates much of the manual work, such as issuing certificate for users, helping user unblock their device PIN, etc.
PKI Use Cases
In addition to multi-factor Authentication, PKI has many additional advanced security functions that can be accomplished using end user devices (smart cards or USB tokens), including endpoint protection (pre-boot authentication and full-disk encryption), digital signature and email encryption.
How Digital signature works
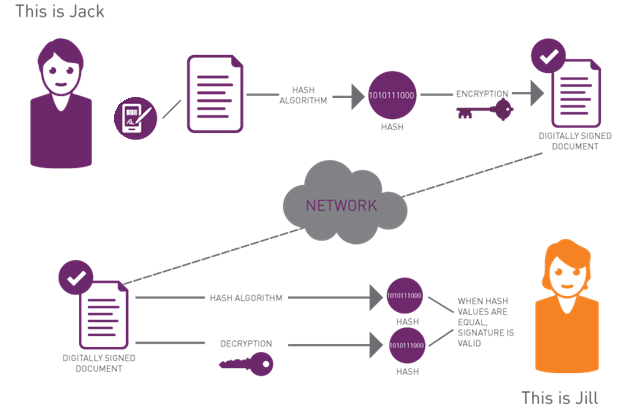
The bottom line
In addition to providing peace of mind that your data, users and systems are protected, PKI provides many business advantages such as:
• Military-grade security: PKI provides the highest protection of your sensitive documents and authentication of your users.
• Additional security functionalities: With PKI, you can encrypt data, disk, and email, as well as digitally sign.
• Solution for compliance with regulations such as GDPR, PCI DSS, DFARS, eIDAS and more.
• Optimized authentication and cost savings: Password management is costly. PKI eliminates the need for users to remember long, complex passwords that they will need to change frequently. A single credential will give users access to multiple applications.
• Improved business processes: Eliminating password protocols will reduce helpdesk calls and an overall IT overhead.


