
Since the dawn of information security, trust has been a critical element. Over time, as information technology has become more distributed, the notion of trust has evolved around who logically needs to be able to access a service. For example, if you are seeking to get onto your corporate network then you will need to have a unique username and password to view the corporate information sources and private documents. In addition, firewalls are used to prevent outsiders and other potential threats from entering these zones.
Nevertheless, only using usernames and passwords to be able to access this kind of corporate information poses problems for those people who need to be permitted to access specific company resources through the internet, such as field engineers. As a result, VPNs have been created to provide trusted communication tunnels that can securely grant access to specific ports of enterprise data, controlled by IT departments.
For a while, this combination of usernames, VPNs, and firewalls was enough to create a high level of security within an organization’s network of employees and external actors. However, this has changed dramatically over the past decade with the explosion of mobile computing. The shift from working on a monitor to a personal laptop and to our devices, like phones and tablets, has proven to be a significant challenge for IT departments. No longer can they call the shots by only allowing corporate data to be accessed through company issued computers.
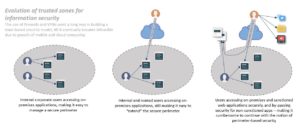
What’s more, this huge proliferation of personal devices has also been accompanied by the adoption of cloud computing and cloud applications, such as Salesforce, Office 365 and DropBox. This means the ways in which sensitive data can be shared has also increased exponentially. In working on projects with other companies it has become commonplace to share files, even for sensitive initiatives like new marketing releases. IT departments have therefore often resorted to blocking any unsanctioned applications or traffic from unmanaged devices. However, the cost of this is excessive and can inhibit innovation within the workforce, forcing employees to use potentially outdated programs and devices that prevent remote working. It is for these reasons that trust-based systems for protecting enterprise information are becoming obsolete.
While hacking corporate network systems from the outside requires a certain degree of skill to break through the firewalls and VPNs, an easier way to gain access to sensitive corporate data is to go via an employee who has access to such data. One such way to do this is via phishing attacks – pretending to be a trusted system to trick an employee into giving over their username and password. Once inside, the hacker can enter the trusted zone and acquire sensitive data or trigger other malicious attacks.
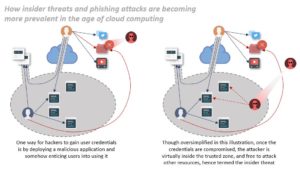
It is this realization of internal threats that coined the term ‘Zero Trust’. This mindset is simple – any user or device trying to access confidential data cannot and should not be trusted by default, even if they work for the company.
When discussing how to implement a Zero Trust framework it must be noted that one size does not fit all in terms of what degree of security needs to be put in place and how segregated access needs to be. However, there are two key enablers that are helpful to take into consideration when adopting Zero Trust posture; Identity and Access Management (IAM) and Network Micro-segmentation.
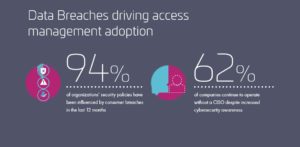
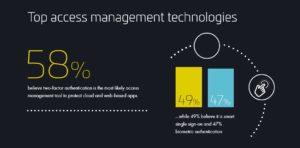
IAM essentially lets system administrators manage the identities of different users and entities; and regulate access to systems or networks based on the roles of individual users within the enterprise. Roles are defined according to job competency, authority and responsibility within the enterprise. A good example of this is the special permissions that more senior figures in the organization may have access to compared to their juniors. In practical terms this may mean that only a Practice Head would have access to the Purchasing System to approve a purchase request. One of the key advantages of Access Management systems is that they can enable or revoke access regardless of a user’s location or device type. This gives system administrators a lot of flexibility in organizations that have a lot of remote or nomad workers; while giving employees the freedom to work from any location. Their value as key resource in cybersecurity is highlighted by the fact that 75% of organizations rely on access management to secure their external users’ logins to online corporate resources.
Network Micro-segmentation works by slicing a network into different segments that can only be accessed by a known number of users. For example, if you worked in HR for your company you could not access the section of documents meant for the Finance team and vice versa. It also means that if a worker’s credentials are used by a hacker, they could not compromise more data than that individual had access to – each application or resource is isolated with its own firewall to secure it. However, although this reduces the lateral movement of threats, a company will still have to use an identity and access management system to identify users, devices and other resources in the first place.
While both these approaches are different, they are complementary in a variety of ways and in the long term most companies will likely need to balance both to significantly reduce the insider threat and create a version of a Zero Trust framework that works for them. As the threat landscape continues to advance and evolve it is important that companies do not forget that sometimes the worst threats come from those you might normally trust the most – the insiders! Never trust, always verify!


