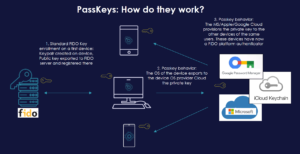
We’ve covered the history of authentication and where we’re at today, but now it’s time to focus on what is to come. We recently saw the release of Passkey, by FIDO Alliance, to support mobile and computer platforms, and with the clear commitment from Apple, Google and Microsoft, the question is no longer if FIDO and Passkeys are going to prevail, but how fast?
FIDO Authenticators, before passkeys
Since the first release of FIDO specifications 8 years ago, FIDO credentials have been identified with some key principles:
- They rely on asymmetric cryptography: A FIDO Authenticator consists of a key pair:
- private key
- public key
- When a new FIDO Authenticator is generated on a supported device, both the private and the public keys are generated on-board
- The public key is transmitted to the FIDO Authentication server
- While the private key never leaves the device
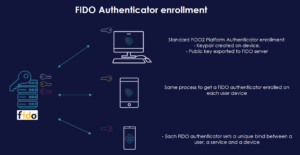
As a result of this, FIDO Authenticator provided a unique bind between service, user, and device. So if a user wanted to use multiple FIDO enabled devices to access a service, e.g. via a smartphone, a tablet and a laptop, the user would have to generate one platform authenticator for each of the three devices.
That´s the way things were, but then in March 2022, FIDO Alliance published a paper introducing the concept of ‘Multi-Device Credentials’ or in industry terms, Passkeys.
What do Passkeys bring?
When it comes to Passkeys, they follow the same principles as their predecessors except for the fourth: the private key leaves the device. It gets uploaded to the corresponding Cloud and from there it propagates to all other FIDO enabled devices from the same ecosystem associated to that user.
So for example, if a user has an iPhone, iPad and MacBook, and generates a Passkey for a given service on one of them, the private key will be uploaded to iCloud and will propagate to the other devices; meaning they won´t have to generate a new passkey for each device – great for the end user!
But it doesn’t stop there – the cloud also has a backup of the Passkeys, solving issues of account recovery and easing access to your services if connecting to a new device via the cloud.
Concerns about Passkeys
Some financial service providers do not feel comfortable with Passkeys. It´s easy to see why if we look at how FIDO Alliance used to advertise the security before Passkeys:
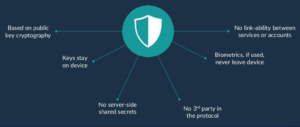
However, with Passkeys half of it no longer applies:
- private keys no longer stay on the device;
- private keys are secrets, now shared with a server; and
- the cloud server is a 3rd party in-between the user and the bank.
There is little doubt that Apple, Google and Microsoft will set high security standards in their clouds to protect Passkeys, but for some financial institutions (FI), it may be a matter of ownership and control.
Even more important, it is yet to be seen if Passkeys can be considered compliant with different regional financial security regulations, such as PSD2 in Europe. So while technology is compelling, concerns are legitimate.
A familiar struggle
As technology evolves, new threats appear, but as do new solutions. While we evolve towards better security and UX, sometimes one is impacted by the other. Our dependency on passwords is as old as the Internet itself, but now Passkeys open the door to break with them for good.
Positive UX of Passkeys will drive demand and ultimately lead to an increase in uptake from service providers, but at what risk to security? There will be, and already are, plenty of talks within FIDO Alliance, regulatory bodies, and other financial industry forums on such topics. Ultimately, as in the past, a compromise will be accepted by a majority, and there will be room for providers like Thales to add on solutions that compensate for the loss of control and downgrade in security.
I hope you enjoyed reading my blog series on the evolution of digital banking authentication – reach out in the comments, or use the contact form to get in touch.
For further reading, visit:
- The Evolution of Digital Banking Authentication – Part 1
- The Evolution of Digital Banking Authentication – Part 2 – The Digital Banking Revolution
- The Evolution of Digital Banking Authentication – Part 3 – FIDO and Passkeys will rock the digital world
- Authentication cloud services to secure access to digital banking