Last month I wrote about alarming trends in eBanking fraud, and how banks are staying ahead of fraudsters. Some of the largest cyber threats have come from Distributed Denial of Service (DDoS) attacks, so this time around I wanted to look at why these are so threatening to banks.
DDoS attacks have reached new levels of sophistication, especially over the past year, and banks which fall victim to such attacks risk a damaged reputation and loss of consumer confidence. Because consumer trust is critical to every bank’s success, banking executives are working harder than ever to protect customers and their data.
A DDoS attack occurs when criminals deliberately inundate web servers with so much traffic at the same time that they cause a site to ‘crash’. There are a number of ways to orchestrate these attacks, which anyone with a keen knowledge of internet architecture can do. Recent attacks have become more effective by harnessing the power of larger networks of computers than ever before.
According to Neustar, DDoS attacks on financial companies have increased 38% from 2011 to 2012. On March 12, six leading US banks were hit on the same day. Just last week, three more were hit.
In April, the FBI reported that 46 U.S. banking institutions had been targeted by more than 200 separate DDoS attacks of “various degrees of impact” since September.
DDoS attacks are particularly dangerous because they could be used to distract security and IT departments while masking a separate, more malicious attack. Some experts suggest that a new type of DDoS attack, which struck two mid-sized banks, might have been a trial for more attacks to come.
Traditional protection, such as firewalls and intrusion detection, is no longer enough. In fact, firewalls actually aid hackers during these types of attacks by becoming the bottleneck that crashes the site. The good news for Banks is there is a whole arsenal of more sophisticated tools being made available today to keep fraudsters at bay.
For the first time, The FDIC (Federal Deposit Insurance Corporation) recently called attention to DDoS attacks, noting that federal banking regulators are reviewing how banking institutions manage DDoS attacks and other cyber security threats. The FFIEC recommends a multi-layered security approach at financial institutions; something they have been recommending for years. So now is a good time to take a look at what type of “layers” are in place and determine if it may be time for tougher security.
Most experts recommend that organizations should employ both on-site and cloud-based DDoS solutions, capable of detecting new attack threats in addition to known ones. Banks should investigate if their network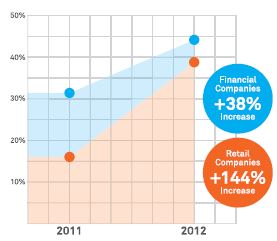 security vendor is up-to-speed on these continued threats and has a roadmap in place for the Bank to adhere to.
security vendor is up-to-speed on these continued threats and has a roadmap in place for the Bank to adhere to.
But not to be forgotten here is the loss of trust that will result with the online banking customer. When a user continues to be locked out of his or her account, by no mistake of their own, they will inevitably become frustrated and wonder if their account is in danger. One powerful way that banks can provide defense and regain the end user’s confidence is by arming them with a “hardened browser” with malware protection. A strong browser with malware protection will not only protect the customer by creating a secure session but also flag any security issues detected prior to entry. For the next tier of security the “hardened browser” can be used on a USB device. Here the secure banking session actually takes place on the USB outside of the Internet – a “cloud” if you will, on a stick for banking customers.
Despite their increasing frequency, the technology to counter DDoS attacks exists, and is becoming more sophisticated. Banks must use every resource at their disposal to ensure that these criminals don’t cause permanent damage to their customer relationships.


