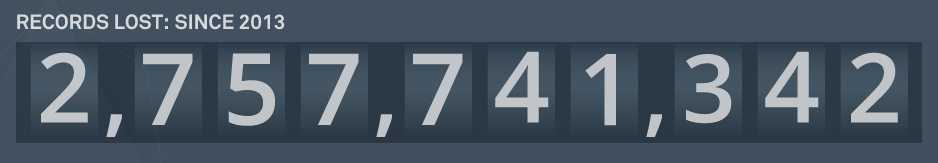
The term data breach has caught the world’s attention, becoming a weekly topic within the news! With over 2.3 billion records reported lost since 2013, trying to predict where the next big data breach will happen seems impossible. Or does it? Surely, enough breaches have now occurred in order to make some hypothesis on what the future holds.
What if Vegas and other bookmakers started taking bets on the next company to succumb to a breach? They would have it down to a science in no time, right? And while making sport out of such devastating circumstances seems trivial, I can’t help but wonder if I’m onto something.
Think about it, the amount of teams (aka. companies) are limitless because a data breach can and will happen to all of them, given enough time.
The wager rests on which companies will have the right strategy in place in order to make it a secure breach and which will not, making tomorrow’s headlines. Pairing companies together and simulating a Vegas-type point spread based upon strengths and weaknesses provides a great model for highlighting the winners vs. losers when it comes to securing data.
Utilizing breachlevelindex.com, a site that collects and analyzes the number of global breaches and lost records, I was able to devise a spread around a couple key factors, increasing or decreasing the odds based on current trends. Then, allowing for the parlay, I created the over and under based on the predicted amount of records compromised.
Key Factors
Industry: Most companies become a target of a breach because of what they do, so type of industry has a strong influence. Those in an industry ranked higher for breaches have to be particularly careful, working extra hard to compensate for this deficit.
Location: Just like the location of where a game is played is crucial, so too is the location of where companies operate. The regions of each company were also factored into my predictions, as well as the compliance standards that are mandated in each country.
Injuries: A team with a stacked roster at the beginning of a season can have their championship hopes ruined by injury and a weak or predictable playbook. Similarly, companies who do not continue to refine their security strategy to accommodate today’s threat vector are not keeping their data healthy and can expect to sustain a loss. Any players (layers in protection) in the line-up not being utilized are treated as an injury, and will receive the necessary handicap.
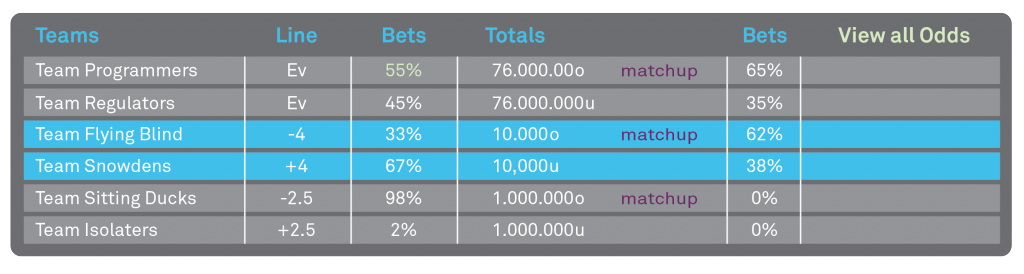
Let’s look at the matchups!
Programmers vs. Regulators
With zero breaches to report, both teams will enter this game with an undefeated record. Utilizing both encryption at rest and encryption in motion has given them the advantage over others in the league that are using a tired out perimeter security defense.
The Programmers however, stand a better chance of sustaining a breach.
Even though Regulators operate in a highly susceptible financial industry, which would normally put them at a disadvantage, due to more disciplined compliance regulations, they are storing their encryption keys within an HSM.
It’s much harder for hackers to obtain the keys within hardware and decrypt data. Programmers have been running on pure luck. Unless they ditch their defensive strategy of natively storing keys within the software for at least a hardened device approach they are going down in flames.
Snowdens vs. Flying Blinds
The Snowdens’ record this season leaves much to be desired. Due to their antiquated approach toward protecting the goods, they’ve already suffered two major internal breaches so far.
Administration got too comfortable, lost sight of who had access to the data, mismanaged keys and by the time anyone realized what was happening it was too late. With an entirely new coaching staff and key management process in toe, they just might turn this thing around.
But, not in time to face Flying Blinds. As long as the Flying Blinds show up with their strong defense, using a combination of HSMs and reliable key lifecycle management they are set. They’ll need to take control early though.
One major weakness of this UK- based team is they get flustered under pressure. They lack the vision that a crypto resource management platform could provide and it’s extremely difficult for them to make changes on the fly if forced to change tactics midway through the game.
Sitting Ducks vs. Isolaters
The Sitting Ducks definitely have the home advantage being located in India versus the Isolaters who are sitting in a hot-bed of breach activity in the US. Both utilize encryption, but Sitting Ducks have left an Achilles heel with unprotecting the data that moves from their headquarters to off-sites locations.
They are not the only team running like this in the league, but it’s an overlooked area that has proven devastating for others this season.
The Isolaters are encrypting everything from databases to cloud servers, but their approach is quite disparate and because of this, the team is not very aligned. With every member of the team so inaccessible and focused on their own island of encryption, it’s impossible to ensure that keys don’t become lost, which is almost as big of an upset as a breach itself.
Conversely, the Sitting Ducks are a well-oiled machine with centralized key management and favored to win this match. Offensively, the crypto processing and acceleration they possess when it comes to secure transactions is what ensures their victory.
Not enough through-put is a strong disadvantage for the Isolaters, as we just watched them choke in the final minutes of last week’s game. Sure, defense wins games, but without a strong enough crypto engine to complete daily transactions this team won’t be able to execute on anything.
Round-up
Albeit, there are plenty of other factors that can be considered such as types of data being protected, and the particular use cases of how each strategy is being employed. (I’ll leave that to the actuaries!)
But one thing is for certain, if organizations started looking at their chances of being breached through a point spread, they could better identify themselves as ‘favored vs. underdogs’ of their industry when it comes to securing data.
Even though these are fictitious companies, the issues they face are real. Thinking of your company as a statistic really draws a correlation between levels of risk versus level of security measures you have in place, as well as highlights the organizations within an industry that are easy prey.
It only takes one small crack in your foundation to take down the entire infrastructure.
Ask yourself, would you bet the house on your organization’s current data protection strategy. Even further, when your customers and prospects are placing their bets, are the odds in their favor?
Hedge your bets
Security is a lot more than finding the right algorithm and cryptography done right is the most secure part of any encryption system. Security deployment should utilize best practices for both encryption, as well key management—creating a Crypto Foundation.
![]() A Crypto Foundation centralizes the approach taken to secure different types of data in multiple environments, combined with the management and maintenance of keys and crypto resources. There are four key areas of consideration:
A Crypto Foundation centralizes the approach taken to secure different types of data in multiple environments, combined with the management and maintenance of keys and crypto resources. There are four key areas of consideration:
- Crypto Processing & Acceleration – Throughput of transactions and number of identities.
Appropriate offloading and accelerating crypto operations will help to avoid processing bottlenecks and increase system capacity. - Key Storage – Securing the key(s) in hardware within an HSM or software within a hardened appliance.
The requirements of your use case(s) and environment will determine the keys’ roles and ultimately how they are stored. For keys that are trusted to protect highly sensitive data and applications, a centralized, hardware-based approach to key storage is recommended. Organizations trying to encrypt mass amounts of smaller segments of data, requiring high availability and usage may gravitate toward a more distributed model. - Key Lifecycle Management – Managing the keys and performing proper procedures and maintenance throughout each step of the lifecycle.
There must be an integrated, centralized approach around generating, storing, distributing, rotating, revoking, suspending and terminating keys for devices and applications. This centralized management platform will perform all key-related tasks and tie back to other systems or HSMs that are performing cryptographic operations using those keys. - Crypto Resource Management – Ability to define access levels, manage and deploy cryptographic resources as well as report on all activity.
In order to ensure consistent policy enforcement, provide transparency, and maintain the health of your system, every organization should have one, easy-to-use interface to configure policies, monitor and report and provision all cryptographic resources.
By factoring these four areas into your strategy, you can provide the consolidation, protection and flexibility that today’s business environment demands.
For more information, visit our Crypto Foundation page.