
Not-so-breaking news: If you expect big data to empower your business going forward, big data security needs to be near the top of your priority list. But what’s the best way to approach it?
Big data trends are dictating the need for new technologies – and consequently – robust security that can withstand the performance and scalability requirements inherent in massive data growth.
It is an undeniable fact that data growth has exploded and will continue to explode; IDC predicts that by 2020 we will produce 44 trillion gigabytes a year. One emerging technology from this trend is the NoSQL database – a hybrid database consisting of traditional SQL schema structures and dynamic alternative structures capable of handling varied data types with efficient flexibility.
This makes NoSQL appealing to many enterprises, and likewise makes NoSQL data security crucial.
NoSQL database security should have layers of defense and include encryption or tokenization at its core. When security is attached directly to the data, components parts of an organization’s defense may fail without rendering sensitive data vulnerable.
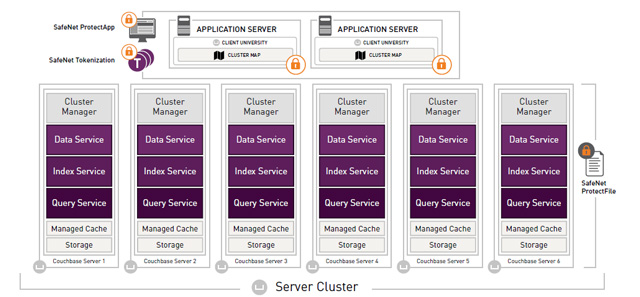
NoSQL database users have several options when it comes to adding encryption and tokenization; most commonly, organizations choose to apply encryption at either the file system or the application level. Let’s explore why.
File system-level NoSQL security
File system-level encryption is an extremely flexible and unobtrusive way of securing sensitive data in NoSQL databases. Such solutions typically will specify which file, folder or share paths require encryption.
This approach allows organizations to segregate their data by sensitivity whereby only data requiring security receives it. Non-sensitive data can be saved to file paths that do not trigger encryption to save compute resources and limit infrastructure complexity.
By bucketing data in this way, encryption solutions can layer access controls to restrict data access according to user, groups or other defined parameters. As an added benefit, by defining security based on folder or share path, any file or object can be encryption – it doesn’t matter if it is an image, database or docker container.
Application-level NoSQL security
 Encryption at the application level has the benefit of securing data earlier in its flow to rest while accommodating a wide range of data types from images and logs to databases and e-mail archives. Since encryption occurs at the point data is being created, it can secure data before other constraints get in the way.
Encryption at the application level has the benefit of securing data earlier in its flow to rest while accommodating a wide range of data types from images and logs to databases and e-mail archives. Since encryption occurs at the point data is being created, it can secure data before other constraints get in the way.
For example, encrypting data in the application can be an ideal way to secure database columns without changing the database’s architecture. When encrypted at this layer, plaintext information is never stored or transmitted which significantly reduces an organization’s attack surface.
At this point in the data flow, organizations can optionally choose tokenization instead of encryption to obfuscate data before storage.
Perhaps, compliance is the security drive and a customer simply wants to remove a database from the scope of PCI DSS – tokenization can be a great alternative to meeting these needs without the performance overhead that comes with encryption.
Compliance and regulatory obligations are one of the biggest encryption drivers for NoDQL databases. Whether it comes from PCI DSS or Sarbanes-Oxley (SOX), often encryption is the mandated solution to securing sensitive customer data. However, the need for security extends beyond simple check-box compliance.
As we’ve seen recently with the recent TeamGhostShell hack of misconfigured MongoDB databases, even well intentioned users make mistakes; it’s natural we’re all only human. However, because we’re dealing with big data solutions any error – no matter how understandable – or vulnerability will compromise massive amounts of sensitive information.
As part of its expanding ecosystem of partners, Gemalto now works with Couchbase to provide NoSQL security solutions that scale with a customer’s big data needs.
By partnering with Couchbase with a portfolio that works at multiple points in the data’s flow from creation to storage, we hope to make it easier for Couchbase customers to add security in the ways that work best for them.
Whether they want the broad and seamless coverage of file system level encryption, or encryption or tokenization to immediately secure data at the application-level, customer should, and now do, have a choice.
 [Click here for full size image]
[Click here for full size image]
Big data solutions are breaking down barriers so organizations can move faster and with greater insight, and security – whether the challenge or the solution – cannot impede that trajectory.
Customers that spend the time identifying where they’re data is located, applying security to that data, and then managing the keys centrally, will go a long way to benefiting from the big data revolution without seeing their names splashed across the front pages for the wrong reasons.
Encryption and tokenization are essential to keeping data safe because they attach security directly to the data and ensure that in the event of a breach (from hackers or from privileged users) sensitive information will not be compromised.
For more information on the new Gemalto and Couchbase partnership, visit https://safenet.gemalto.com/partners/couchbase/.


